The Joy of IPv6
by Sam Bowne
I am a mad IPv6 advocate.
I teach computer networking at City College San Francisco (CCSF), and I am adding it to all my classes next semester. If you want to understand computer networking, you need to learn IPv6. And I recommend that you start soon.
This article introduces IPv6, explains why you need it, and how to get started with it quickly and easily. And, of course, a few tips on hacking it.
What's Wrong With IPv4?
Most Internet-connected devices are still using the older IPv4 addressing scheme, which assigns each device an address like: 147.144.1.212
This translates to a 32-bit binary number, so there are a total of 232 possible IPv4 addresses - approximately 4 billion.
And that is simply not enough. We have almost 7 billion people on Earth now, and they all need cell phones, iPads, RFID tags in their shoes, and, soon, Wi-Fi-enabled Google brain implants.
Various tricks like Network Address Translation (NAT) have been used to stretch the inadequate IPv4 address space, but they are not sufficient to allow the Internet to grow as it must.
The IPv4 address space is almost completely full.
At the time of this writing, only sixteen "/8" address blocks remain of the original 256, and they are expected to be all allocated during 2011 or 20121.
After that, no more fresh addresses will be available, and people will be reduced to buying used addresses from other, smarter, companies who already switched to IPv6. CCSF has an entire Class B allocation, by the way, and my current asking price is $1 million. Call me.
IPv6: The New Frontier
So IPv6 was created.
IPv6 addresses are longer and written in hexadecimal notation, like this: 2607:F128:0042:00AA:0000:0000:0000:0002
Omitting unnecessary zeroes makes the address easier to write: 2607:F128:42:AA::2
This address has 128-bits, so there are 2128 of them, which is more than 256 billion billion billion billion.
That is a lot more sensible - an addressing scheme that has enough room to accommodate all the devices we expect to create for centuries, even if Moore's Law continues that long.
Is This Just Hype?
Until a few months ago, I thought we could safely ignore IPv6, because we could continue to stretch IPv4 with NAT and also re-purpose the reserved Class D and E addresses for general use.
But I was wrong.
ARIN, the organization that controls IP addresses, has announced that they will not use Class D and E addresses to prolong the life of IPv4 - when the addresses run out in 2011 or 2012, it's GAME OVER.
Imagine inventing some awesome new gizmo like heads-up Internet sunglasses or a holographic game people play with tattoo-implanted OLED displays, manufacturing 50 million of them, and finding out that you cannot connect them to the Internet because the Internet is full.
The Dept. of Defense converted to IPv6 in 2008, after years of planning and preparation3.
The rest of the US government will complete their conversion in 20124.
Google is on IPv6 at ipv6.google.com, and Facebook is at www.v6.facebook.com. IPv6 is mandatory. Ignoring it will only make you obsolete. You might as well stick to your 300 baud acoustic coupler.
How to Get Started With IPv6
Most ISPs don't offer IPv6 for home customers yet.
So you are probably limited to IPv4 right now. But just because your ISP is not ready yet, that's no reason for you to wait. You can use IPv6 immediately over any network with a tunnel - sending IPv6 packets inside IPv4 packets.
I have used three free tunnel brokers for this purpose. The simplest and easiest for Windows users is gogo6.com. If you want to try other services, these tips may help:
- SixXS has a package called AICCU available for OS X, Linux, and UNIX, but the Windows GUI version does not work with Windows 7 - you have to use the older CLI version.
- Hurricane Electric Free IPv6 Tunnel Broker provides tunnels, but they use Protocol 41, which is neither TCP nor UDP and is blocked by most home routers.
Fun and Games: IPv6 Certification
Hurricane Electric has a series of certification tests to show proficiency with IPv6.
These are fascinating, challenging, and fun! You get a badge (see Figure 1) and even a T-shirt if you make it to Guru level.
Here are the levels:
- Newbie: Knows basic facts about IPv6.
- Explorer: Has the ability to connect to servers via IPv6.
- Enthusiast: Has a web server delivering pages over IPv6.
- Administrator: Has an SMTP server that accepts mail over IPv6.
- Professional: Has reverse DNS correctly configured for the IPv6 address of your SMTP server.
- Guru: Nameservers have AAAA records and can be queried over IPv6.
- Sage: Has IPv6 Glue.
Every company will need to perform these tasks within the next few years. I learned a lot getting these certifications - I had not even heard of "Glue" records before.
Privacy Risks in IPv6
In IPv4, most people use private IP addresses which are translated to public addresses shared by many people.
So if you do something naughty, like download copyrighted music, it's not easy to prove who did it. But in IPv6, the MAC address of your interface is included in your IPv6 address, unless you implement "Privacy Extensions."
Windows, however, uses "Privacy Extensions" by default.5
Hacker's Toolkit
THC-IPv6 is available from freeworld.thc.org/thc-ipv6, and includes a nice suite of hacking tools for IPv6.
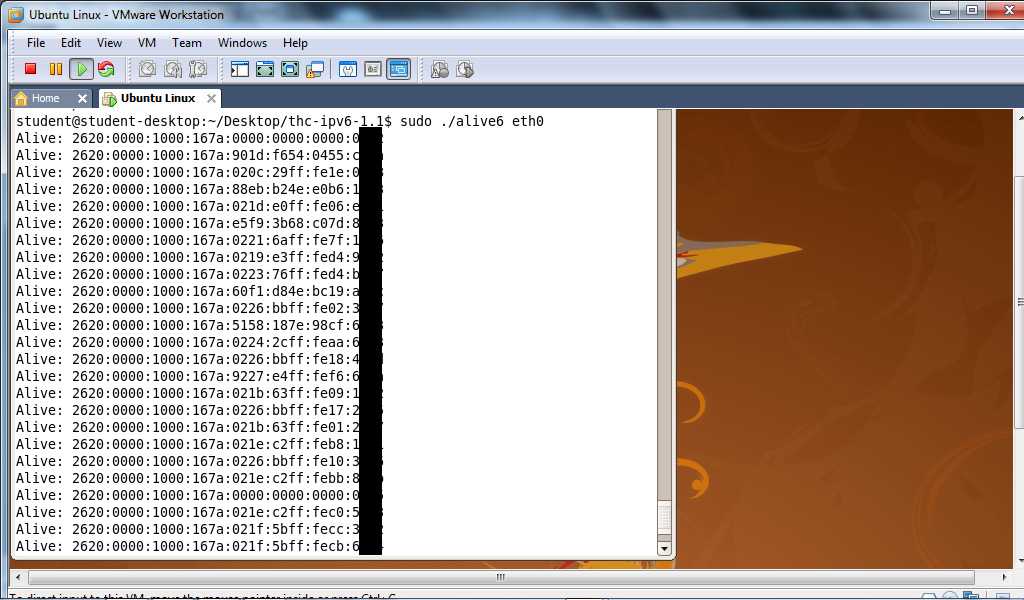
I went to a conference where they provided a native IPv6 wireless LAN, and scanned it. I found 30 hosts, as shown in Figure 2. For instructions to help you install THC-IPv6 on Ubuntu Linux, see ref. 6.
Other IPv6 Hacks
Most security devices are not yet IPv6-capable.
That makes it open season for people who are ready to use it. You can run BitTorrent over IPv6, which will probably bypass any traffic shaping, Deep Packet Inspection (DPI), or security devices in your way.7
Rogue Router Advertisements or DHCPv6 servers can be used to deny service to clients, or to perform a man-in-the-middle attack.8
A single malicious packet sent into a point-to-point link can flood it with echoing "destination unreachable" responses.8
And "Routing Header Zero" IPv6 packets can be used to create loops and amplify traffic to perform a Denial-of-Service attack.9
Patches exist for these known attacks, but there will be many more found as IPv6 deployment progresses.
Altar Call
The End Is Near!
Don't bury your head in the sand - get on board the IPv6 train now!
There's a lot to learn, especially since we will all need to use both IPv4 and IPv6 for at least a decade. And the boundary between the two systems will be a natural weak spot, where exploits will be found and defeated.
You may choose to ignore IPv6, but your enemies won't. People who start now can become experienced professionals, ready to help others when the chaos of rushed transitions begins.
For More Information
An excellent source for starting out with IPv6 is "IPv6: What, Why, How" at www.openwall.com/presentations/IPv6.
The book IPv6 Security by Scott Hogg and Eric Vyncke is highly recommended by experts - I haven't received my copy yet, so I can't give you my opinion.
If you want to reach me, use Twitter @sambowne, or email sbowne@ccsf.edu.
Have fun with IPv6!
References
- IPv4 Address Report
- Beware the Black Market Rising for IP Addresses
- IPv6 in the Department of Defense
- Federal IPv6 Transition Timeline
- IPv6 Deployment on Production Networks
- Scanning for Hosts on IPv6
- utorrent app now supports IPv6/teredo directly
- The ping-pong phenomenon with p2p links
- RFC 5095: Deprecation of RH0