

Note
http://support.google.com/accounts/bin/answer.py?hl=en&answer=1066447
https://www.microsoft.com/sk-sk/store/apps/authenticator/9wzdncrfj3rj
$ setenforce 0 $ rm -f /etc/localtime $ ln -s /usr/share/zoneinfo/Europe/Bratislava /etc/localtime $ tzselect (Europe) (Slovakia) (Yes) $ ntpdate pool.ntp.org $ rpm -Uvh http://zeus.fei.tuke.sk/bps3r/epel6.rpm $ yum -y install google-authenticator mc
$ cp /etc/pam.d/sshd /etc/pam.d/sshd.old
$ mcedit /etc/pam.d/sshd
auth required pam_google_authenticator.so
auth include password-auth$ mcedit /etc/ssh/sshd_config ChallengeResponseAuthentication yes$ /etc/init.d/sshd restart
$ useradd -m google $ passwd google
Warning
$ su - google
$ google-authenticator
Note
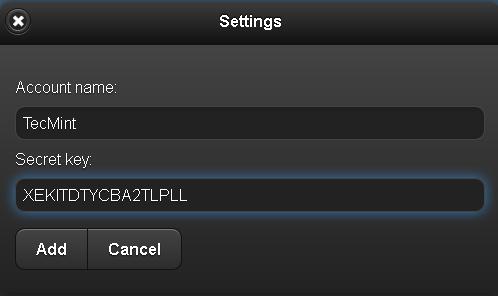
Your new secret key is: ABCD12E3FGHIJKLMN
Your verification code is 98765432
Your emergency scratch codes are:
01234567
89012345
67890123
45678901
23456789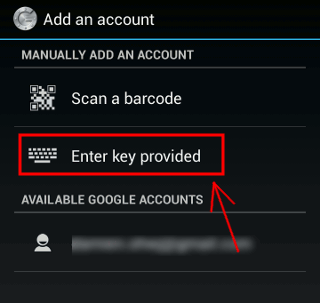
$ ssh google@localhost