![[Contents]](contents.gif)
![[Index]](index.gif)
The Inferno system hides network complexity from applications. When an application wishes to access services that reside on remote servers, a few simple operations are used to construct a single, locally-represented namespace that may encompass multiple machines and multiple networks.
Like other services in the Inferno system, network interfaces are represented as file systems in a local namespace. The Styx communications protocol unifies different parts of the local namespace that may be constructed from the vast collection of files on the network. File operations between any two machines are accomplished by sending requests and receiving replies via Styx messages. The protocol supports remote access to files and allows a remote machine to use these interfaces as gateways.
Styx messages are not manipulated directly by an application developer. Any file operation generates the appropriate Styx messages to perform the necessary operations on the namespace. The exact sequence of messages differs depending on the call, but the complexity is concealed from the developer, who simply invokes familiar open, read, and similar file system operations.
Styx runs on top of any reliable transport level protocol, making the underlying network connection transparent to applications. Styx relies on several properties of the underlying transport protocol. For example, it assumes that messages arrive reliably and in sequence.
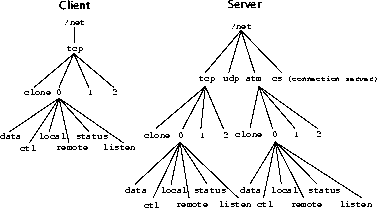
Figure 1-3 shows the /net file tree for a client that only has access to a TCP/IP connection. The /net file tree on the server called <server> has access to multiple connections.
$ mount net!server /n/remote $ bind -a /n/remote/net /netAfter the mount and bind commands have executed successfully, all of the listed networks that are connected to the <server> are available to the client. The client can now send requests intended for these networks via the server. The server thus acts as a gateway without the need for a client protocol stack.
Following the mount / bind sequence described above, a list of directories at the client machine would look like the following:
$ ls /net cs atm udp tcp tcpNote that there are two /net/tcp directories resulting from the union of the local and remote directory structures. Both the local and remote versions of this directory are part of the local namespace. Only the first, on the local machine, is accessible; using the -b option in the bind command would make only the remote /net/tcp directory accessible.
The Inferno server application named Cs hides the details of call setup from applications. Cs is provided as a demonstration server application.
A network connection is established in two phases. The Cs application is first contacted to translate a logical network name into a device name and a connect address string. The Cs service reads a logical name such as tcp!<server>!styx and writes the device name and connect address string:
/net/tcp/cloneThe path name identifies the network device; the connect address string is used to set up a connection. To establish the connection, the client then opens /net/tcp/clone and writes the control message into it.
connect 35.104.9.52!6666
When /net/tcp/clone is opened, it actually returns a file descriptor to:
/net/tcp/<number>/ctlwhere <number> is a numeric directory name
(Figure 1-3). Text commands are then written to the ctl file to control the connection.
Each network directory contains a clone file and a directory for each connection of that type, numbered 0 through n, where n+1 is the number of connections of a single type. Opening the clone file finds and reserves an unused connection directory and opens its ctl file. The file descriptor returned to the client by the open call points to the ctl file. Each connection directory contains files to control a single connection and to send and receive information to it.