Why Aren't You Cracking Your Users' Passwords with Real-World Data?
by Sardonyx
This is not going to be another "How to Crack Active Directory Passwords" article. There are plenty of how-to's on the Internet that can show you how to do that. This article is meant to show you the real-world data that proves cracking your users' passwords is a good idea.
I had a great supportive boss who would indulge a lot of my crazy ideas over the years. When I went into his office to ask for $2,000 to build a password cracking box, he didn't hesitate to say, "Hell yeah, that sounds dope!" I work for a midsize healthcare organization with about 3,000 users. I've been a systems administrator for ten years and have been specifically dedicated to information security for five.
Like it or not, the world runs on Microsoft Active Directory. Ninety-nine percent of companies out there use it as their central authentication system. While most of the world is trying to move to "password-less" solutions, I have yet to hear about anyone successfully migrating 100 percent of their applications. The password is still king. Plus, like I said, I work in healthcare, bro, and healthcare is always ten years behind everyone else, and many small- to medium-size organizations are in the same boat. Passwords are going to be around for a long time, and we all know that users suck at them, so why not do what we can to help make them better?
This story starts in 2015 with an organization that had a very very bad password policy: minimum six characters with complexity, rotated every 90 days. The nurses and docs hated changing their password every quarter, even with those lax restrictions. I knew it was a bad policy, and I had to prove it to management. So I grabbed a copy of our domain's NTDS.DIT, threw it at a Radeon R9 270X, and cracked away.
18,000 passwords later, I had cracked almost 80 percent of them. These are the main user logins, admin passwords, service account passwords, passwords that would get you access to protected health information, the works. So I made a presentation with this data for my management, and they agreed - the password policy had to change. This had to go to the top, though, and that took about two years to get fully implemented. This was around the time that NIST came out with the major changes of no password rotation and to check passwords against a "known bad password list," so that was what we did: minimum 12 characters, no password rotation, and checked against our bad password list In the meantime, the sysadmins agreed that we needed to do something about infrastructure accounts and administrative users, so we upgraded those passwords as soon as we could, which took a few months.
Fast-forward a few more years - I was dedicated to information security full time. I got back to cracking. With the new password policy in place, a dedicated sysadmin team with management buy-in, and an unused account purge, I ended up only cracking about 17 percent of our 12,000 accounts. The trend continued with 13 percent of 15,000 accounts the next year (2020). The following year, we implemented cybersecurity training and made it mandatory for all users, and I ended up cracking about 12 percent of 17,000. Users are going to be users, and with tools like Pipal, it's easy to see the trends and terrible base-words that people use, so we add them to our password blacklist.
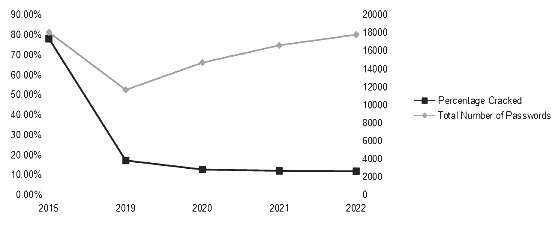
The graph is pretty clear - we're constantly adding users, but keeping our total percentage of passwords cracked trending down. No, it's not perfect, but my boss met with our cybersecurity insurance firm, and they commented that they had never heard of any organization doing this kind of data trending, which gave me the thought for this article.
So, why aren't you cracking your users' passwords?