What's Old is New Again: PDF Malware Part Deux
by lg0p89
Years ago (yes, "Get off my lawn!") when the industry was growing by leaps and bounds with new vulnerabilities weekly, and businesses were getting pwned for bragging rights and not tens of thousands of dollars, the innovation was to weaponize PDFs.
This worked for a while, and defenses were put in place. This held for the most part until recently. The attackers are using the PDF in a slightly new way. They secure a target list, which these days is relatively easy and cheap. There have been so many breaches over the recent years, this isn't a problem. This coupled with some company websites listing their management with their email addresses makes this much less complicated.
With this in hand, the attackers send an email with the ill-intentioned PDF.
This nuance started to be seen in 2020 and used the title "Remittance Invoice.pdf".
That should have been enough to keep the users from opening it, but you know...
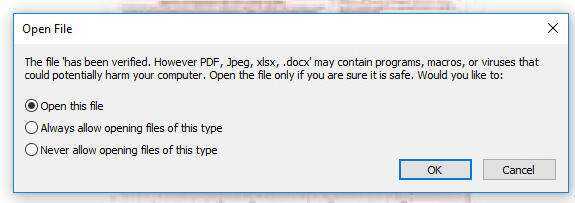
Within this is an embedded Word document titled:
has been verified. However PDF, Jpeg, xlsx, .docx |
As this has been used over the last two years, the file name may have changed to something still catchy that would entice the user to click, double-click, or even triple-click the file. Yes, users still re-open the same files even after they know overtly and clearly that they are infected. I once ran an international phishing campaign for a global company. There were users who clicked the blatant phishing email, received the "You've been caught" landing page, and still went back clicking away. I guess they just wanted to make doubly sure they screwed up.
I digress.
The PDF file name needs to be something that will draw the attention of the targets. You could also use IRS Notification, Proposed Bonuses, or any title that makes people believe they'll be able to see some data or information that they shouldn't have access to (thank you social engineering!).
Let's address the Word document title.
This is embedded in the PDF file. The name itself is a little odd. For all the available choices, why this one? This all becomes clear operationally when you open it.
Normally, when the user attempts to open it, Adobe Reader displays:
The file '[file name]' may contain programs, macros, or viruses that could potentially harm your computer. |
When the user opens this, the message then reads:
The file 'has been verified. However, PDF, Jpeg, xlsx, .docx' may contain programs... |
Let's say your PDF name is:
Nobody may contain programs, macros, or viruses that could potentially harm your computer |
When the user opens it, they see:
The file 'Nobody may contain programs, macros, or viruses that could potentially harm your computer' has been verified. However, PDF, Jpeg, xlsx, .docx... |
See what it does?
For a user that doesn't know to look for this, or is too tired from working too much, the sneaky aspect of this might not be caught. They may breeze through the warning and check and find out too late what they did.
In the instance when the file is opened, which is completely plausible, it disables the protected view and the user is a happy recipient of malicious activity.
Within the Word document is a URL used to load an Object Linking and Embedding (OLE). This contains code written to exploit CVE-2017-11882 for remote code execution.
The code directs the system to download fresh.exe, which is a keylogger (Snake).
Curiously, you could use this method of delivery for other malware.
For the users thinking PDFs are safe, no worries, just open them, share this with family and friends - not so fast.
This is still an issue. While this uses an old framework, the low-tech yet creative addition has the opportunity to really mess with your users.