Has the CIA Cloud Service Become More Secure? Negative
by Duran (Hong Kong)
Lately, the U.S. intelligence community has been gradually migrating their business to cloud services.
The CIA already did cloud work with Amazon several years ago. The CIA's former chief technology officer for the chief information officer Gus Hunt also revealed in an interview four reasons for the transition to the cloud: "speed, efficiency, innovation, security." Of course, the first three reasons aren't in doubt, but the last one - security, really?
The answer is in the headline. Security is not a good reason for migrating to the cloud, at least in my perspective. Why do I say this? Hmm... You need a pre-knowledge list here:
- James Clapper Jr.: "'Double-digit' Cuts Coming for Intel Budget" Washington Post, October 17, 2011)
- "What to Cut and How to Cut? Historical Lessons from Past Reductions in the Intelligence Community" (Capstone Project, RAND IPC, 2012)
- "Transparency Takes a Hit in CIA Budget Cuts" Sunlight Foundation, 2013)
- "The Details About the CIA's Deal With Amazon" The Atlantic, 2014)
- "Securing the Cloud" Journal of Information Warfare, April 2014)
Once you have read the above materials, follow my analysis on them.
First, in the book Permanent Record, Edward Snowden told us he was building some cutting edge technology for the CIA's private cloud with his contractor partner in 2011 when he was in the U.S.
Please take note of the time period. It was the moment when the U.S. government made a decision to cut the intel budget. Director of National Intelligence James Clapper said that "He was going to try to 'protect people' and that he hoped to find 'one half the savings' by reducing overlap among the myriad computer systems now operated by the 16 intelligence agencies that make up the community." Clearly, the CIA had already made a plan for budget cuts, using cloud services to solve the "silos" problem - "The problem of having a billion buckets of data spread all over the world that they couldn't keep track of or access."
Second, the Bush School of Government and Public Service made a capstone report for RAND IPC.
In its "Recommendations" section, it says, "A decrease in manpower without corresponding reductions to the tasks assigned to the IC creates ineffectiveness, as evidenced by the Korean and 9/11 case studies." and "Policymakers should be aware of the danger of exacerbating the collection-analysis balance. Personnel reductions must be accompanied by corresponding cuts to intelligence missions. If this prioritization does not occur, the IC will be overwhelmed with data, and will lack the ability to process the data in a timely and actionable manner." And, "When policymakers cut personnel, they should be wary of the assumption that analysts are completely fungible. Technical and regional expertise is highly valuable, and assuming an expert in one field can move to another field and perform effectively is unrealistic."
Overall, we can see this report does not advocate personnel reduction, so the Intelligence Community (IC) have to turn to seek efficiency from science and technology. This represents "speed, efficiency, innovation."
Third, the more secure cloud is not real. Why is that? Everybody knows the safest way to store something is to lock it in a vault, whether it's gold or information. We usually make a paper copy of important files in daily life; people always think that virtual things are unreliable. The ultimate object representing the wealth of a country is gold bars.
"The Amazon-built cloud will operate behind the IC's firewall, or more simply: It's a public cloud built on private premises." The saying from the article "The Details About the CIA's Deal With Amazon" from The Atlantic actually told us the IC data center facilities were located in a safe place, which can be verified from the paper "Securing the Cloud:" "C2S is housed in a private data center on government premises."
Obviously, the agency is very concerned about the physical security of the facility. Besides, according to the description in "Securing the Cloud," it seems that the task of cloud security is left to NSA: "NSA's Information Assurance Directorate (IAD) is heavily involved in projects related to security for cloud architectures to meet the future computing needs of the Intelligence Community. NSA is leveraging this technology for optimum advantage while providing confidence in data security." and "As part of its IAD mission, the NSA will continue to provide expertise for protection of U.S. National Security Systems whether the data is stored in traditional physical computing systems or cloud-based virtual systems."
It is funny to read the word "confidence" in that sentence, it can be seen that the security of cloud services is indeed a complex and severe problem. In this article, the author enumerates various security issues, which is worth reading.
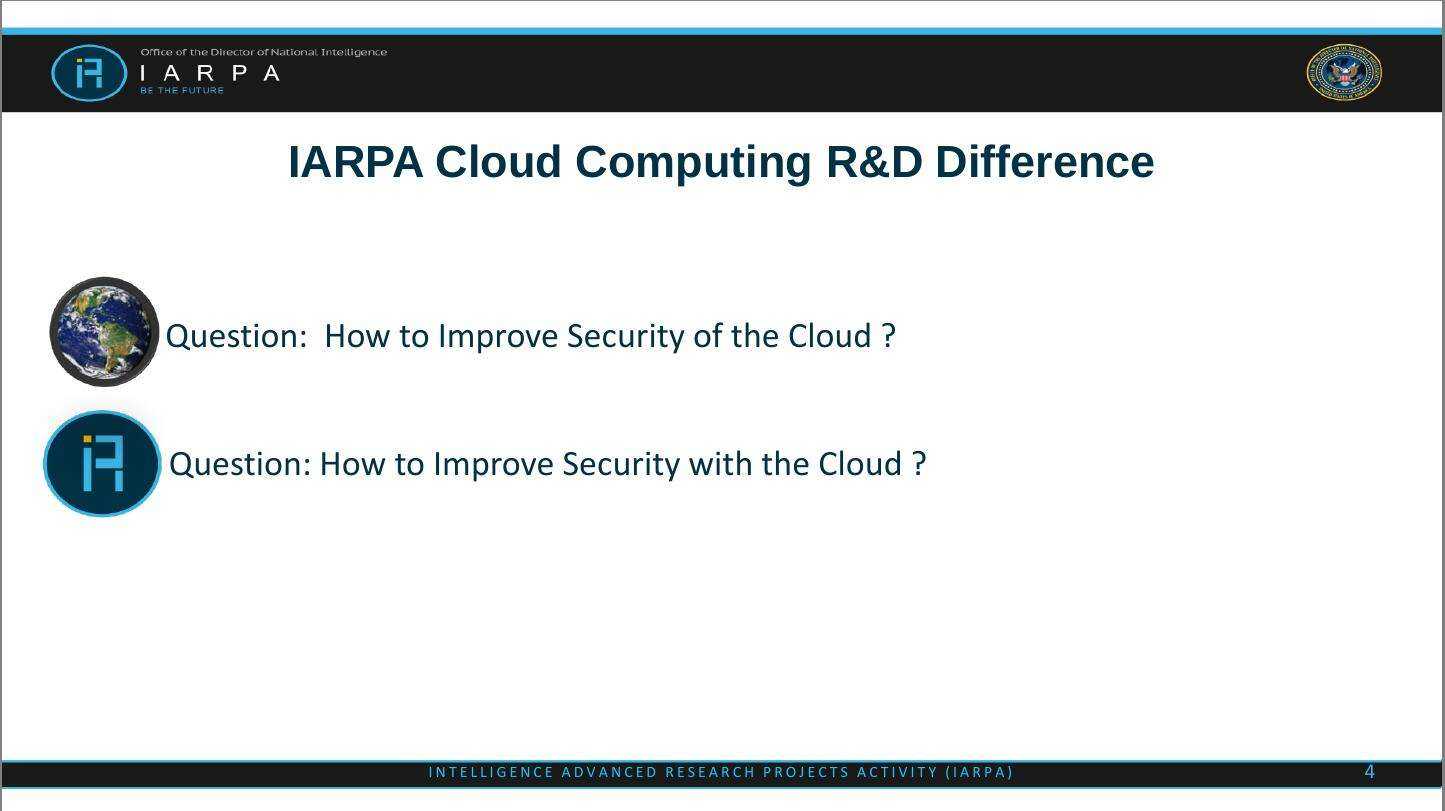
Additionally, Intelligence Advanced Research Projects Activity (IARPA) from DNI's Office also tries to convince the public about the cloud security problem. Its explanation mainly illustrates a question "How to Improve Security with the Cloud?" More interestingly, they proposed a concept "Defining Protection Benefits/Costs as a Function of Time" in the slides.
Finally, let's look at some evidence that was obtained from the Department of Energy.
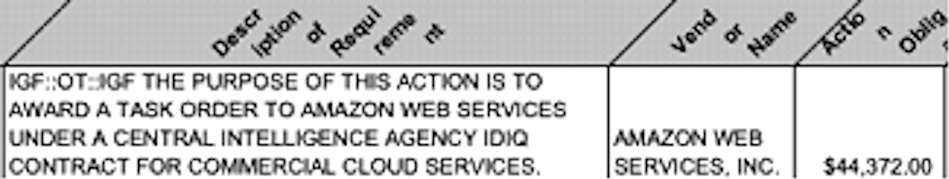
Numbers tell it the best. The cloud service budget increased from $44,372 in 2014 to $1,247,284 in 2021.
This is just the budget of the CIA. It shows the CIA cloud business growing rapidly and this will increase in the future. The government can slash the budget through data center integration, even at the expense of being criticized for cutting off some units (such as the CIA's Historical Collections Division). However, they still have to pay larger costs on cloud security, including hardware and software, as well as "Redesign the Legacy User Environment Leveraging AWS EC2."
Snowden wrote in his book that, "The aim was to unite the agency's processing and storage while distributing the ways by which data could be accessed. In plain American, we wanted to make it so that someone in a tent in Afghanistan could do exactly the same work in exactly the same way as someone at CIA headquarters."
It is true that the United States can use its super technical power to do something, but the strongest fortress was broken from the inside. More advanced and intelligent things do not mean more security. Legacy systems are often reliable, which has been proven with countless facts.
Besides, if an employee can access it from Afghanistan, so can the enemy.