Understanding Election Security Through the Lens of the Hierarchy of Voter Needs
by Allie Mellen
In the book A Theory of Human Motivation, Abraham Maslow laid out a motivational theory in psychology that he describes as an attempt to formulate a positive theory of human motivation. This is called Maslow's "Hierarchy of Needs," and the theory can be extended to the motivation of individual citizens to vote based on what needs are or are not being attacked: The Hierarchy of Voter Needs.
Using this hierarchy, we can better understand what attacks limit individuals' ability and motivation to vote and why.
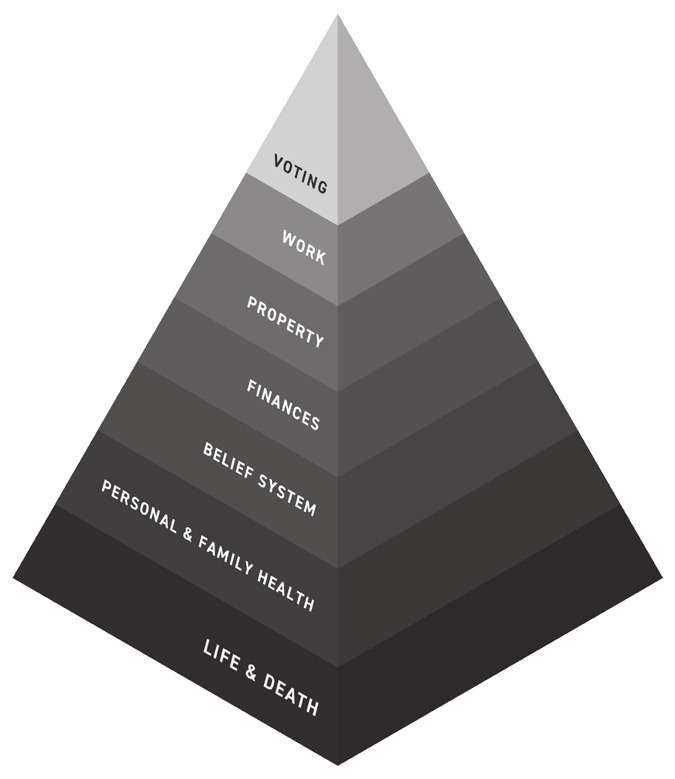
The "Hierarchy of Voter Needs" can be defined as the hierarchy of needs that must be secured before an individual can be motivated to vote.
Each level of the Hierarchy of Voter Needs compounds on the other. For voters, events of life and death come before voting. When citizens are facing a natural disaster that threatens their lives, voting will not be their priority - getting to safety will be. Similarly, personal and family health, work security, property security, and financial security all tend to be prioritized before voting to different degrees.
But how do we understand voter needs in the context of cybersecurity threats?
Relating Cyberattacks and the Hierarchy of Voter Needs
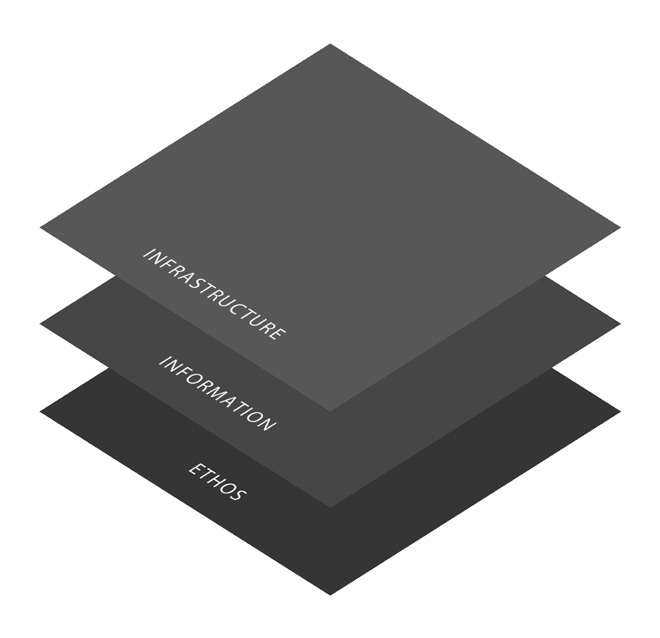
To clearly categorize cyberattacks on voters and democracy, we can use a valuable framework that clarifies the targets of cyberattacks. Cyberattacks target three different planes that human beings operate on:
- The Infrastructure Plane is the one we consider the most often with regards to daily life. This is attacking machinery, whether it be voting machines, the electric grid, traffic lights, or other physical elements.
- The Information Plane is the difference between facts and fake news. This can be particularly difficult to address as compared to other planes, and often relies on legitimate individuals spreading disinformation they believe to be true. Often, this can be fueled by emotional triggers.
- The Ethos Plane is about swaying and shaping public opinion. It's shaping the perception of reality for large groups of people to the point where they will advocate for a particular opinion. This is often done through the manipulation of social networks with botnets and sock puppets.
With election security and existing infrastructure considerations, we have focused our preparation efforts on attacks to:
- The infrastructure plane. However, as we have seen in previous elections, attacks that target.
- The information plane.
- The ethos plane have not only been widespread, but have also contributed to the degradation of citizens' faith in democracy.
Attacks on the infrastructure plane most clearly affect all levels in the Hierarchy of Voter Needs. Attacks on the information and ethos planes, however, tend to be digital actions with few direct physical attacks, mostly focused on the belief system. It can be difficult to quantify the damage caused by digital attacks like spreading misinformation or swaying public opinion. However, over time, the results of these attacks can be clearly mapped to the hierarchy, as we have seen with previous attacks.
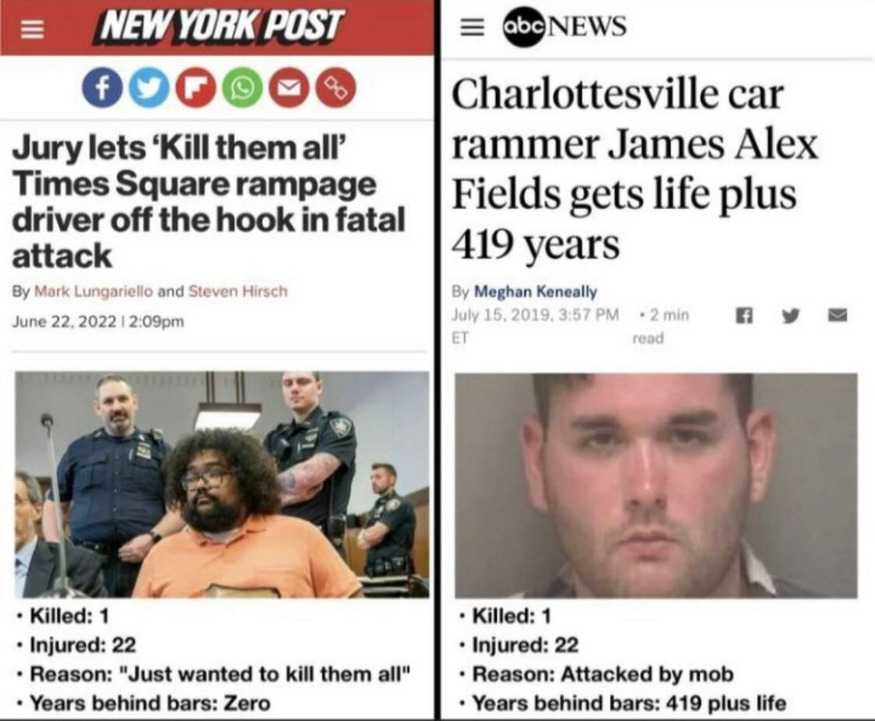
For example, an attack on the ethos plane to strengthen public opinion against a particular race or religion can lead to public upheaval and action, as we saw in 2017 with the "Unite the Right" rally in Charlottesville, Virginia. These attacks on the ethos plane lead to an attack on the foundation of a citizen's needs, the needs of protecting against life and death circumstances.
James Fields Crash Video This video shows landwhale leftist, Heather Heyer, who was "murdered" by James Fields by running her over during his "hate crime." Unfortunately for the prevailing narrative, that WebM shows the car didn't even hit her. The coroner's report stated she died of a heart attack. It's yet another example of the bullshit of this case. As the mob surrounds Fields, he tries to get away but realizes the two/three vehicles in front are actually parked and not moving. So he does the only sensible thing while being attacked, and reverses out.
Professor Who Chased Charlottesville Driver with Gun Attacks Camera Man
Just as with Maslow's Hierarchy of Needs, the different levels can blend together at times. Voting may be worthwhile if you feel it will help you gain financial security. Similarly, voting may be a way you exercise your freedom to maintain your property security. However, the main point of the hierarchy remains. If the foundation is attacked, the higher levels lose priority. To what extent depends on the gravity of the situation and surrounding factors.
Why Make this Hierarchy?
This hierarchy helps us identify all the different things voters need to worry about, and therefore, all the things attackers can target. When defending elections, we need to be cognizant of the fact that election security extends far beyond hacking voting machines and can have a far deeper and longer lasting impact. Without establishing a hierarchy like this one, we would be unable to effectively lay out and dissect the different kinds of threats election security might face, especially those unexpected or more difficult to predict. This can serve as a model for red and purple teams looking to give the public and private sectors valuable insights into what types of threats they should be prepared for.
Allie Mellen is a security strategist at Cybereason. She has spent several years in cybersecurity and has been recognized globally for her security research. Over the past two years, she has helped organize and execute multiple election security tabletop exercises with participants from the FBI, Secret Service, Department of Homeland Security, and state law enforcement. In these sessions, it's hackers versus law enforcement as an exercise in what attackers can do to disrupt Election Day and what the government is prepared to do - or should be prepared to do - to stop them.