Responsible Disclosure of a Malware Infiltration Attempt
by The Piano Guy
Lately I have noticed that the articles in 2600 are skewing towards the more advanced.
In a way that is a good thing, because a decent percentage of the 2600 reader population can comprehend that, work with it, and use it well. At the same time, my perception is that there are still people who, like I did over 20 years ago, are just coming to the hacker community as non-experts interested in learning more.
Today I received a novel attempt to infect my computer (clearly they failed). Maybe it isn't novel to you, but it is the first time I've seen this. It occurred to me that a write-up on what happened, how I analyzed it, and how to act may be useful to the newer members of the readership. No huge revelations today, but useful to some. Also, the best way to respond (at least in my opinion) if something like this should happen again.
Last January I had a need to hire a contractor.
There is a referral service in my local area, akin to Angie's List, but more honest because one can only get in by multiple positive referrals; buying a listing is not allowed. I picked a dozen vendors, sent out a blanket email to all of them with a link on Facebook to the work I wanted done explained well (to keep the email size down), and my phone number.
As an aside, I got very few responses, and none of them panned out. So that didn't work out so well.
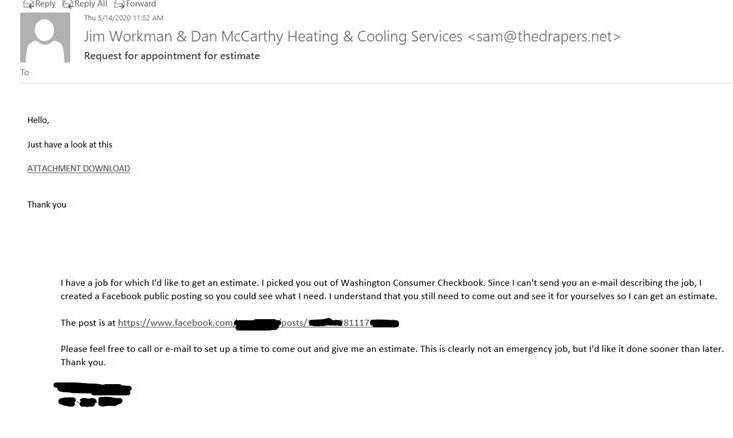
Today (May 14, 2020), I received an email quoting the body copy I sent out, with this direction:
The company I was sending to wasn't the one listed, the email didn't match that anyway, and I knew better than to click on the file attachment.
That, and it was months late. At the same time, it was novel for a malicious actor to break into a company, look through their emails, quote their requests for quotes back to the customer that sent them, and then send them malware.
That does increase the trust level a bit, and I can see some of our less informed friends and relatives say to themselves, "Well, it's not some random person, it's a response to an email I sent, and this is their answer."
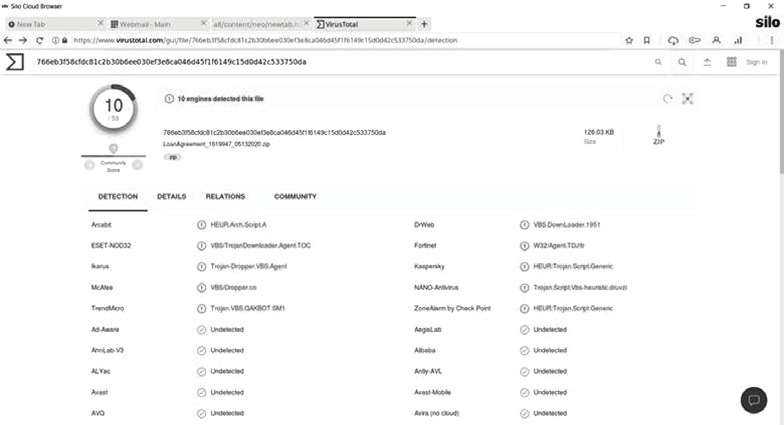
Wanting to see more about what was going on, I opened up Authentic8 Silo, logged into my email, downloaded the attachment, and put it through Virus Total.
No surprise what the results were:
While I think anyone reading this either already knew what Virus Total was, or does now.
Authentic8 Silo may be a different story.
They provide a secure browser as a service, which lets a user surf the web without leaving a record, and with nothing being transferred to the local machine except pixels (unless seriously intentional choices are made).
It's only $10 a month for an individual account and has some nice security features built-in. I don't know if I get a spiff for referring people, but if I do I'll put an advert in the classified section next quarter with a referral code or something.
Of course, if you need it now, go get it and don't worry about me on this. You can't just buy it online; they have to talk to you first, but it's harmless. They are trying to assure that people are not using their service for malicious purposes. Authorized penetration testing is not considered malicious.
After I knew what I had here, I decided that I should let the people who had their computers infiltrated know.
After all, they should let their customers know to not click on the link. Of course, I sent the same email out to a dozen companies, and if you look at what was sent back to me, it's not possible for me to tell who was hacked.
So I sent out an email to everyone I wrote in January saying that they should check their computer systems to see if they have any sent emails to me today. Also, that even if they didn't, they should check their systems for infiltrations.
In my email, I did provide a phone number to answer more questions, but I made it absolutely clear that I wasn't asking them to click on a link, I wasn't asking them for information, and that I wasn't looking to make them a cybersecurity client.
By doing none of that (and loudly doing none of that), there was no way to infer an ulterior motive on my part, or for them to think that I was hacking them.
About a half hour later, I received an email from one of the companies telling me to, "Replace the existing Noritz tankless water heater with a Navien tankless water heater. Install will include service valves and gas shut off valve to the unit. First responder discount given along with all other discounts. Code:20FRHW."
I was angry, as I was trying to help them and I got this as a response.
I wrote back, "DID YOU EVEN READ MY E-MAIL? You may have been hacked. I'm doing you a favor to tell you so, since I do cyber for a living. Sheesh!"
I got a reply with an apology telling me that they just sent me the wrong email, and that they were sending an email out to all of their customers saying, "Please do NOT open any attachments from Jim Workman and/or Dan McCarthy, we are working with IT to fix the issue. Sorry for any inconvenience."
I replied with a thank you for the clarification, and realized that I had two more steps to take.
I sent another email to everyone else I wrote earlier today letting them know that another company had acknowledged that they were the infected company (so they could stand down), and I knew I had to write this article.