A Guide to ALKEMI
by Ronald Gans
This article is about my program, ALKEMI, which I recently completed.
ALKEMI encrypts your text data up to 12,000 characters and in most languages to the format of HEXASCII, an ASCII representation of binary data. So, for instance, the hexadecimal value 0xFE (which is 254 in decimal) would be represented as FE (without the quotes). The hexadecimal value 0x27 would be 27. All 8-bit binary data (that is, data values like 10010110) can be represented as two-letter hexadecimal values. The binary value 00001001, which is decimal 9, would be represented as 09, and so forth.
Here's how it works: Type or paste text into the Original Text box up to 12,000 characters. Any language that uses characters is O.K., including Chinese, Japanese, Hindi, Hebrew, Arabic, English, etc.
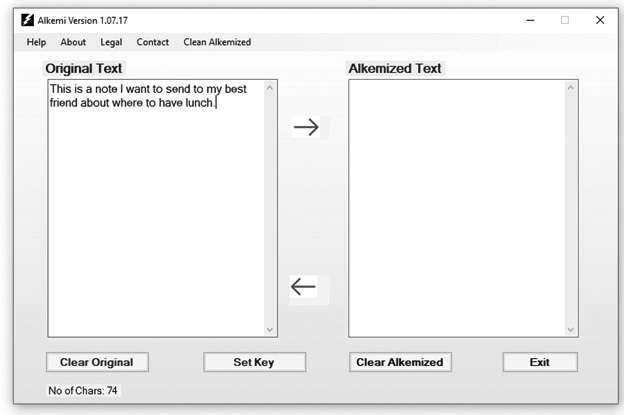
Choose your key. This is the key you can share with your friends. It can be up to 32,765 characters long and, again, any character set is O.K.:
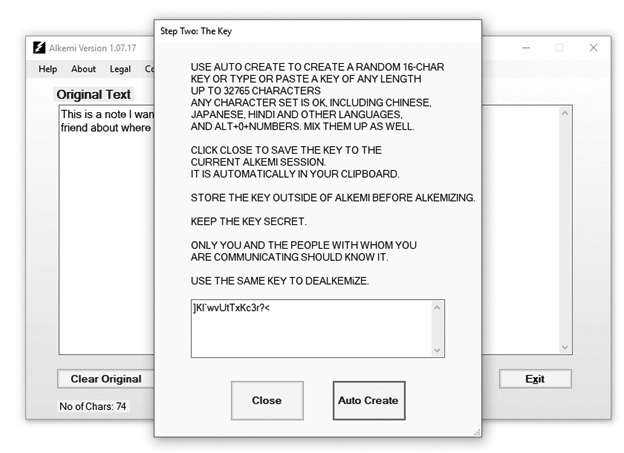
Then just click the right-pointing arrow:
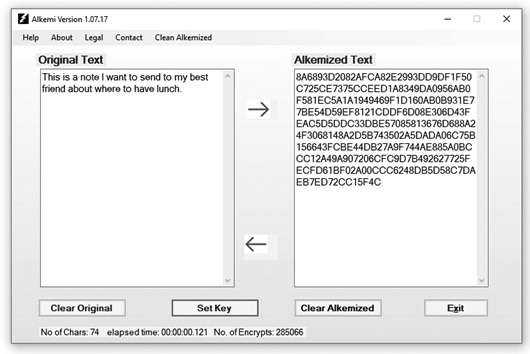
Being just text, it can be sent anywhere text can be sent, like Twitter, email, etc. You can tweet your followers with the Alkemized text and, since only they have the key, only they can decrypt it. Text data, of course, is just data like anything else.
In today's world, snooping is nearly ubiquitous. Not only do the intelligence agencies of various countries examine data (mostly in transmission), but so do many email providers, mostly to monetize your communications. So I wrote ALKEMI to help protect communications from such snooping.
ALKEMI uses an encryption format I created between 2005 and 2018, about which I wrote an article "Yull Encryption" published in Vol. 32, No. 4 in 2015.
The encryption is not mathematical, unlike AES and others. It relies upon 64 routines which are called hundreds of thousands up to millions of times. Routines do things like XOR a byte array, or take a byte array and move lower or upper nibble around the array. Mostly it works on a subset of a read array. It might take a subset of that:
void rotateArrayLeftAsBits(ref byte[]inB)
{
if (inB.Length == 0)
return;
byte[]outB = new byte[inB.Length];
byte[]bits = new byte[inB.Length];
int i;
for (i = 0; i < inB.Length; i++) {
if ((inB[i] & 0x80) == 0x80)
bits[i] = 1; // save the high bit for later
outB[i] = (byte) (inB[i] << 1); // SHIFT LEFT ONE
}
// now add in the saved high bits
for (i = 1; i < inB.Length; i++)
outB[i - 1] |= bits[i];
outB[inB.Length - 1] |= bits[0];
// copy back into inB
System.Buffer.BlockCopy(outB, 0, inB, 0, inB.Length);
}
|
Some procedures create a byte array based on the values from the key, others from a "matrix" like extraction:
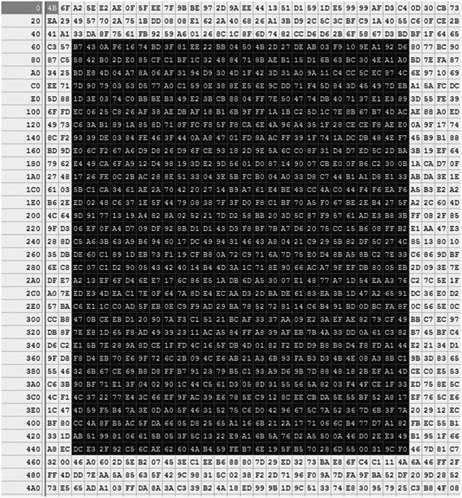
The black rectangle represents a possible "matrix." That is, extracted data, which is clearly no completely sequential. It will start at some offset into the read buffer, run so long, then go to the next "line" (not a real line but some designated amount; this graphic only helps visualize the process).
Some byte extractions take data from the read buffer parameter in a more disjointed fashion:
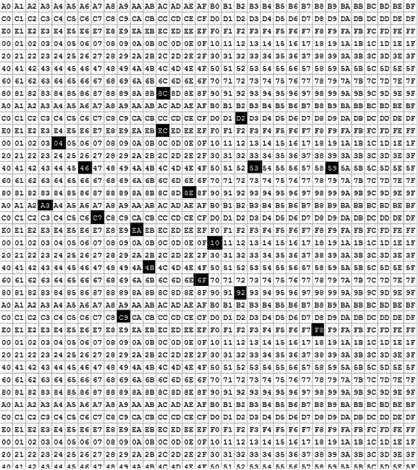
The reads (of the original text data) are prepended with pseudorandom characters using:
byte[] b = new byte[sizeofRandomData]; new RNGCryptoServiceProvider().GetNonZeroBytes(b); |
Since the Microsoft TextBox control supports a large number of character sets, ALKEMI can encrypt Chinese and other languages the same way:
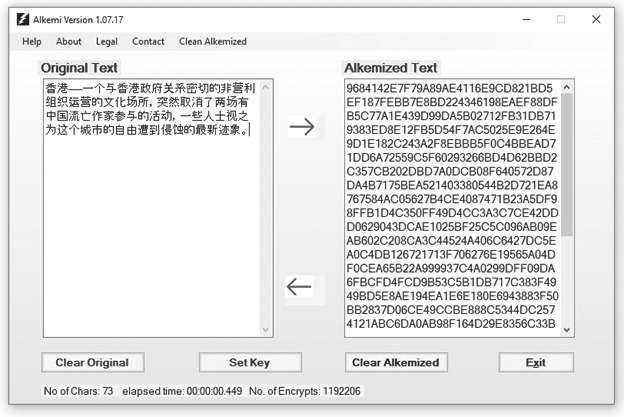
I think I've made ALKEMI easy to use. When you encrypt (or decrypt), the data is also placed in your clipboard so you can, in two steps, encrypt and paste into a communication program. The same with the key. When you create the key, it is also placed in your clipboard as soon as you close the dialog box so it's easy to save (like with Notepad or Notepad++) and communicate it to your friends.
ALKEMI does not protect its process from side-channel attacks. There is some code which is there to mislead intruders, but not a lot. I think I've protected the executable from reverse engineering to the extent any code can be protected. At one time I used Confuser, which I thought was quite good, but Windows flagged the confused app as malware. I use another protection app called the Phoenix Protector.
I hope you take a look at the executable ALKEMI.EXE and find that it might be quite useful - I'm thinking specifically for people in countries where the government is not all that friendly. ALKEMI can also hide data from eager monetizers like Verizon and Google.
I welcome any criticism, comments, flames, kisses, whatever.
The ALKEMI website is at alkemized.com. I'm working on a Facebook page which is at www.facebook.com/Alkemi-301561457306680.
The name ALKEMI means nothing. I just sort of like it. I have been writing code since the mid 1980s, starting with assembly language, C, C++, C#, etc., mostly in the financial sector in New York City.