Bypassing Email Anti-Spam Filters
by Sentient
This story is from a while ago, shortly after I graduated with a bachelor's in information security, I landed a job at some flashy consulting firm.
The job was to consult companies on how to improve their security. My first engagement was to perform phishing against a set of 150 employees across the company's offices around the world.
Naturally, I started performing Open-Source Intelligence (OSINT) against the organization to learn everything possible about their operations - upcoming announcements, key personnel, branding (fonts, colors, etc.).
Leveraging the information obtained, I created a beautiful email template, and an associated credential-harvesting website. Our client contact commented that the email looked almost too good, and that we may need to dumb it down a bit. I was ecstatic.
Before launching the phishing attack, it is always a good idea to test the attack with your client contact to ensure that everything is working as expected, that they agree with the method of attack, etc. We sent our test email, which discussed a new company roll-out, and directed recipients to login to our phishing site. We waited. The client contact never received the email.
Upon some digging by the client, they identified that their anti-spam solution immediately flagged our email.
The initial email and phishing website had everything necessary configured to prevent this. For the website, we leveraged certificates purchased by a genuine and reputable company. For the emails, we had set up Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM).
SPF is another type of DNS record used to describe what mail servers could send emails from a given domain1.
DKIM is where each email sent contains a digital signature validated against the public-key published in the domain's DNS records2.
Our email had the proven authenticity that could bypass Google's, Microsoft's, and even my own company's anti-spam filters - but it was not enough to reach the client.
* * *
Let us take a brief detour into determining the status of both SPF and DKIM of an email.
First, open Google Mail. If you are using Inbox by Google, open an email, click the sideways ellipsis, and click "<> Show Original".
If you are using plain old Gmail, open an email, and click the downward pointing arrow, then click "Show Original".
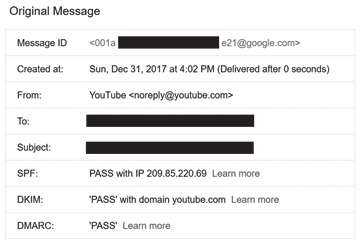
This will display a screen showing how Google Mail has validated the email's SPF, and DKIM records.
Below is the result of Google attempting to validate the records of an email from YouTube. As you can see, the email passed with flying colors:
I read every bullshit marketing guide on how to evade spam filters, learning in the process that email marketers have a real problem with spam filters. This led me to tweaking the email in every regard to bypass the spam filter.
None of these tweaks worked.
I needed a radical new approach.
In the shower one morning, it finally hit me. The way to defeat the spam filter was so easy, it was staring me in the face. Google can help find answers to questions, but this time the answer was Google. There was no way this would not work.
I quickly bought a new domain, and threw it on a Google for Work (GFW) account.
GFW is essentially the Google-suite of tools (think Google Mail, Docs, Drive, etc.) sold to businesses or individuals looking to use them more professionally. One of the main benefits is that GFW allows the use of a custom domain, and easily provisions new accounts to leverage said domain. Perfect.
GFW also comes with an extensive API, allowing anyone to build a quick and dirty script to automate the sending of emails. To prevent you pesky marketers from spamming the world, I will not be posting the script here!
I re-sent the phishing test email to the client contact, leveraging the GFW email infrastructure, and they successfully received the email. We defeated the spam filter! Now we could commence the attack. Discussing with the client, we decided to choose a future Monday morning (FYI, there are many different strategies for when to phish, so your research/situation may differ).
The morning of attack arrived.
I was sitting in a hotel restaurant with a coworker eating breakfast. With the email sending script primed and ready. I took a deep breath. Nerves started to creep up. A rush of questions flooded my mind. "What if no one clicks a link?" "What if all the requests DoS the site?" "What if this flood of emails trigger the spam filters?" I exhaled and pressed Enter.
I did not look away from the screen, and the anxiety built.
With rate limiting, the script took exactly 20 minutes to finish. A few minutes passed. Then an alert popped up.
A user clicked the link, and entered their credentials. Then two more. There was an incredible flood of responses. The relief washed over me, allowing me to finish eating.
Periodically through the day, I kept checking back to see how many hits I got, feeling small bits of excitement with any new hit.
The attack would end up being a resounding success, so much so that it defined the team's phishing methodology going forward, and paved the way for many future phishing engagements.
References
- About SPF - support.google.com/a/answer/33786
- About DKIM - support.google.com/a/answer/174124