Bluetooth Hacking 101
by Chuck Easttom
Introduction
Bluetooth is ubiquitous.
You probably sync your phone with your car via Bluetooth. That is just one example of how Bluetooth technology can be found throughout our daily lives. Laptops, smartphones, tablets, cars, and all sorts of devices are Bluetooth-enabled. It is my hope that you will read this article with an eye towards testing the security of your own Bluetooth devices, rather than trying to breach others' Bluetooth (which is a crime).
The Bluetooth standard was developed by the Bluetooth Special Interest Group, which includes over 1,000 companies including Siemens, Intel, Toshiba, Motorola, and Ericsson. The IEEE standardized Bluetooth as IEEE 802.15.1, but no longer maintains the standard. The main advantage of Bluetooth is its ability to discover Bluetooth devices that are within range. This is precisely why it has become so common.
Bluetooth is a type of near field communication (i.e., limited range) that operates at 2.4 to 2.485 GHz and uses spread spectrum, frequency hopping at 1,600 hops per second. For readers not familiar with spread spectrum frequency hopping, that essentially means that the signal is hopping between frequencies in a given range. Bluetooth devices have a 48-bit identifier assigned by the manufacturer that is similar to a MAC address for a network card.
As an interesting aside regarding Bluetooth, the name comes from King Harald Bluetooth, a tenth century Danish king. He united the tribes of Denmark, thus the implication is that Bluetooth unites communication protocols. There have been different explanations for his name. One was that he had a bad tooth that was blue (i.e., rotted). Another explanation was that he was often clothed in blue.
Many texts and courses teach that Bluetooth has a maximum range of ten meters. However, that is only partially true. In fact, it is only true for Bluetooth 3.0. The following table summarizes the ranges and bandwidth for the various versions of Bluetooth:
Version Bandwidth Range 3.0 25 Mbit/s 10 meters (33 ft) 4.0 25 Mbits/s 60 meters (200 ft) 5.0 50 Mbits/s 240 meters (800 ft) |
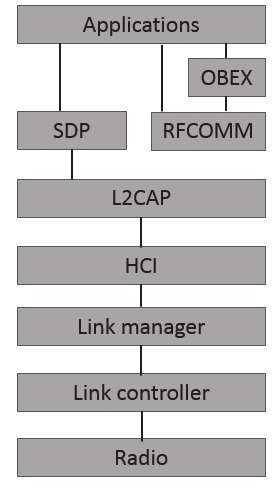
Bluetooth is designed as a layer protocol architecture.
This means there are layers of protocols being used. The mandatory protocols that all Bluetooth devices have are LMP, L2CAP, and SDP.
LMP: Link Management Protocol is used to set up and control the communication link between two devices.
LCAP: Logical Link Control and Adaptation Protocol is used for multiplexing multiple connections between two devices.
SDP: Service Discovery Protocol is how two devices find out what services each offers.
RFCOMM: Radio Frequency Communications, as the name implies, provides a data stream. In this case, it is a virtual serial data stream.
BNEP: Bluetooth Network Encapsulation Protocol is used to transfer some other protocol over the L2CAP channel. It is encapsulating the other protocol.
AVCTP: The Audio/Video Control Transport Protocol is used to transfer audio visual control commands over the L2CAP channel.
HCI: Host Controller Interface refers to any standardized communication between the host stack (i.e., the operating system) and the controller (the actual Bluetooth circuit).
OBEX: Object Exchange facilitates the transfer of binary objects between devices. It was originally designed for infrared, but is now used by Bluetooth. This is used in accessing phone books, printing, and other functions.nbsp; It uses RFCOMM for communication.
The main protocol stack is shown in the following image:
The Bluetooth Special Interest Group unveiled Bluetooth 5.0 during an event in London on June 16, 2016.
This version of Bluetooth is primarily focused on the Internet of Things.
When you pair your device with another via Bluetooth, they exchange a bit of information including device name and list of services.
Bluetooth security defines four modes. Clearly, which mode your phone is using will have a great impact on what attacks will and won't work.
Security Mode 1 is non-secure.
Security Mode 2 controls access to certain services and uses a security manager. But this is only initiated after a link is established.
Security Mode 2 has three levels:
- Level 1: Open to all devices, the default level.
- Level 2: Authentication only.
- Level 3: Requires authentication and authorization. PIN number must be entered.
Security Mode 3 initiates security procedures before any link is established. It supports authentication and encryption. The NIST considers this the most secure.
Security Mode 4 requires authenticated links, but like Mode 2 only initiates the authentication and encryption after a link is established.
Bluetooth Attacks
Now that you have a general idea of how Bluetooth operates, let's take a look at some of the attacks one can perform on a Bluetooth device. Bluetooth attacks are quite common, so let's begin with a brief summary of the common attacks.
Contrary to what you may have seen on television and in movies, forced pairing a Bluetooth device is actually quite difficult and will only work with a really insecure device. However, there are attacks that can be done. This should familiarize you with what can be done to a Bluetooth-enabled device.
- Bluesnarfing is a class of attacks wherein the attacker attempts to get data from the phone.
- Blusnipping: This is a variation of Bluesnarfing. It works at longer ranges and was described at DEFCON in 2004.
- Bluejacking is sending unsolicited data to a phone via Bluetooth. This is sometimes used to send spam instant messages.
- Bluesmacking is a denial-of-service attack wherein the target is flooded with packets.
- Bluebugging remotely accesses phone features. This may seem very similar to Bluesnarfing, but the goal with Bluebugging is not to get data, but to activate certain phone features.
- Bluesniffing is the same thing as war driving. The attacker is trying to find available Bluetooth devices to attack.
- Blueprinting gets its name from foot printing. In the case of Blueprinting, the attacker is trying to get information about the target phone.
Bluetooth also provides an alternative way to access laptops. Most laptops are Bluetooth-enabled. This provides a possible avenue of attack on the laptop. It just so happens that many organizations block a variety of computer connections (CD/DVD, USB, etc.) to prevent users from either installing files or exfiltrating data. However, many of these same computers that have USB blocked have Bluetooth working. That would provide another pathway to exfiltrate data or install software.
Bluetooth Tools
There are a number of tools that an attacker can use to facilitate a Bluetooth attack. You should be familiar with at least some of these. Some tools are only for Android, others for iPhone, and some for both.
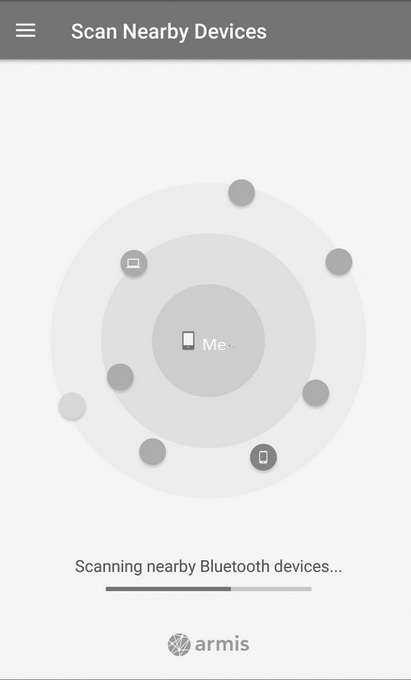
BlueBorne
This is a vulnerability scanner for Bluetooth. It is available in the Google Play store for Android phones, and you can see it at: www.armis.com/research/blueborne/
The vendor also has a white paper on Bluetooth vulnerabilities.
You can see the tool in the following image:
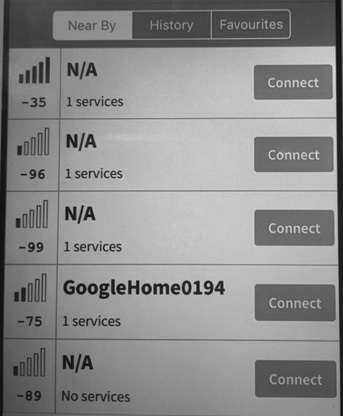
BLE Scanner
This tool is for the iPhone and is a free download. The first thing it will do is show you nearby Bluetooth devices.
You can see this in the following image:
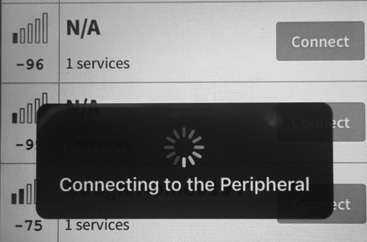
Then simply click the connect button to attempt to connect to that device. This is shown in the following image:
Pally
Pally is another Bluetooth scanner for the iPhone. It has an easy to user interface and will provide you basic information about nearby Bluetooth devices.
This can be seen in the following image:
There are a number of other tools one can find for either scanning Bluetooth or even attempting to hack into Bluetooth. It is important for a penetration tester to have a suite of tools and techniques at his or her disposal. The entire goal of a penetration test is to try the same techniques you believe an attacker would use.
Here is a list of some other tools:
- PhoneSnoop
- Bluescanner
- BH BlueJack
- Bluesnarfer
- btCrawler
- Bluediving
- Bloover II
- btscanner
- CIHwBT
- BT Audit
- Blue Alert
- Blue Sniff
Conclusions
Bluetooth, while very convenient, is susceptible to a number of attacks.
And there are a lot of tools to help someone attack a Bluetooth device.
This article just scratched the surface of Bluetooth security, but hopefully it was enough to get you started studying this topic.