What Happens When WHOIS Data is Made Public
by Victor
It could be because of clumsy fingers (or a crummy mobile site), but whatever the reason, if you left accurate personal information publicly exposed on a WHOIS record, what would happen?
I wanted to find out - hypothetically speaking.
Double-Check to Make Sure to Tap the Correct Target... You Probably Want "Private"
Who's WHOIS
WHOIS is a lookup service administered by various domain name registrars who must provide free access (via a website and programmatically) to domain name registration data. In theory, the WHOIS protocol exposes a standard interface for retrieving information associated with a particular domain name.
For instance, if you wanted to purchase "allaboutfrogs.org" from its owner, your first step would probably involve pulling up the relevant WHOIS record. Or if you thought you owned a copyright involving "allaboutfrogs," the WHOIS record is the first legal point of contact.
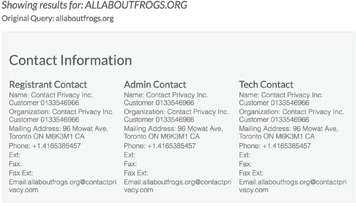
But if you actually look up the WHOIS record for allaboutfrogs.org however, all of the information is in fact concealed:
The WHOIS system itself dates back to at least the 1980s (back to even the pre-Internet ARPANET days) when there existed a perhaps quaint notion that any user connecting to a WHOIS-like system could be trusted.
The Internet Corporation for Assigned Names and Numbers (or ICANN, a SoCal-based non-profit which effectively administers the "bones" of the public Internet) currently has a toothless - and accordingly useless - WHOIS usage policy wherein users:
"Agree not to use this [WHOIS] data (i) to allow, enable, or otherwise support the transmission by email, telephone, or facsimile of mass unsolicited, commercial advertising, or (ii) to enable high-volume, automated, electronic processes to collect or compile this data for any purpose, including without limitation mining this data for your own personal or commercial purposes."
Since there is virtually zero chance of this policy deterring bad actors or abusers of the WHOIS system, domain name registrars have set up various "cloaking" services in which a WHOIS lookup on a domain will simply return the contact information of the registrar itself and not of the user who actually purchased/manages the domain name.
The only reliable way to peek through a WHOIS cloak is with a court order or a domain-name broker with a check in hand. Some registrars charge money for this type of cloaking service while other registrars throw it in as part of the registration fee.
But what happens if you don't use a cloaking service? What if you actually exposed your contact information to the open WHOIS system?
Becoming John Spamee
I opened a sterile Yahoo! account (whoisfun@yahoo.com) and created a "clean" disposable burner telephone number. After some back-and-forth, I settled on the honeypot's name to be whois-is-fun.com.
I even came up with a name: John Spamee.
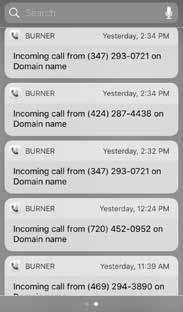
Exactly what happened next is a bit hazy, but clumsy fingers could have slipped and potentially inaccurate information briefly (and also tragically publicly!) made its way into the WHOIS system:
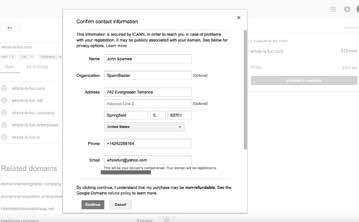
This Demonstrates a Different WHOIS Problem goo.gl/4r6aCG
The Yahoo! email address was used solely for this transaction and the burner phone number did not seem to be on any preexisting SMS spam lists. The machine was clean and there was zero public mention of whois-is-fun.com itself. It was a ghost.
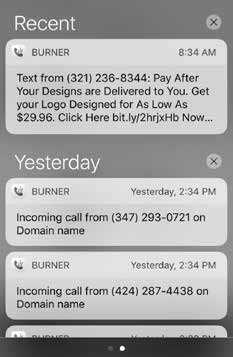
After marking WHOIS data as "public," you'll quickly start to hear from many helpful new friends who are all very eager to get in touch by any means necessary:
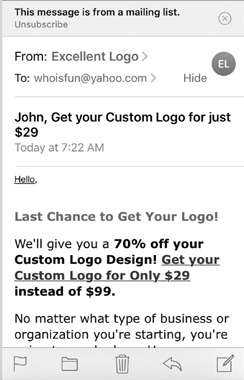
While most firms did not seem to want to work very hard when they made their pitch, quite a few went to the trouble of implementing a friendly, "Hi there, ${first_name}" personal touch:
So What?
Of course, none of this is surprising. For one thing, WHOIS in its current form exists only to facilitate legitimate "business" like domain name transactions or to handle various legal disputes and problems. It was never designed to be impervious to automated scraping or telemarketing software.
For another thing, the folks performing WHOIS spam appear to mostly be interested in booking work or clients. The notion of chasing down recent domain registrants is not necessarily a terrible one if used as a component of a lead generation strategy for a scrappy SEO/WordPress firm.
While not a bad idea on paper, one could imagine in practice that WHOIS spamming is not very effective/profitable for any particular firm since there are so many other sharks in the same ocean chasing the same fish. (Probably mostly just fish who left their WHOIS details public.) Regardless of its effectiveness, if WHOIS spam is as low risk and low effort to pull off as it seems, it makes plenty of sense why firms would continue to employ it.
Even if not surprising, the fact remains that if a registrant in 2017 provides accurate contact information for their WHOIS record and neglects to use a third-party cloaking service, that user is in big trouble. They will be completely inundated with spam and "offers" - not to mention they will also greatly increase their exposure to identity theft risk.
In its current form, the deficiencies of WHOIS are not solvable with a couple of patches or touch-ups. A lot of the problems with WHOIS are undergirded by a base and probably unsolvable "people" problem: how do you convince strangers to behave a certain way when it is not in their economic interest to do so and especially when there is no creditable penalty mechanism to punish bad actors?
WHOIS Reform: RDS
At the time of writing, the public recommendations from ICANN regarding WHOIS spam include the following:

"You may want to contact the registrar of the spammer's email"
To be sure, ICANN certainly does not exist in order to fight spam. It's simply not part of ICANN's job or related to any part of its charter. That said, ICANN is undoubtedly aware of the deficiencies in the current WHOIS system (ICANN identified leaky data as just one of the many problems associated with WHOIS). As part of a very long bureaucratic journey, ICANN's then-CEO Fadi Chehadé in February 2013 convened the Expert Working Group on gTLD Directory Services (EWG) to study proposals to try and fix the crucial WHOIS system by starting from scratch.
There are a number of ideas coalescing from the EWG's report, but perhaps the most intriguing is an expansive vision of what a next-generation Registration Directory Service (RDS) WHOIS replacement could look like.
One promising component of the RDS vision is a doctrine known as "purpose-based disclosure." Susan Kawaguchi (Domain Name Manager at Facebook) explains it this way: "When you get to the front door you don't get to just walk in, you have to tell us [admin] who are you and what are you using this for [...] if you want to know someone's personal data you have a duty to provide your own."
Under an RDS scheme, there will still be public data that is always available just like with the WHOIS system today (dates, statuses, etc., etc.) and nothing much will change there. What is different, however, is that certain types of registration data will become designated as privileged or "gated." Instead of harassing the owner on the WHOIS record, a "real" attorney with a need-to-know can get access to the site's legal contact data (the same for technical or financial issues). Gated data is therefore only provided to accredited people or their representatives who have (1) verified their identity and (2) verified their legitimate need to know.
The actual details are still being worked out (and will continue to be for some time), but RDS with purpose-based disclosure might solve exactly the sorts of problems that WHOIS as currently constituted is incapable of solving. In the meantime, be sure to cloak those WHOIS records or look into PRQ (prq.se).
Further Reading
- tools.ietf.org/html/rfc920
- www.scientificamerican.com/gallery/early-sketch-of-arpanets-first-four-nodes/
- simonecarletti.com/blog/2012/03/whois-protocol/
- www.reuters.com/article/us-yahoo-nsa-exclusive-idUSKCN1241YT
- www.securityskeptic.com/2014/11/debunking-myths-about-domain-registration-data-whois-accuracy-obligations.html
- www.livescience.com/20727-internet-history.html
- www.darpa.mil/about-us/timeline/arpanet
- whois.icann.org/en/history-whois
- webmasters.stackexchange.com/a/14773
- blog.easydns.org/2014/01/21/icann-unleashes-deadliest-ddos-attack-vector-of-2014/
- archive.icann.org/en/meetings/costarica2012/bitcache/Transcript_%20Replacement%20of%20WHOIS%20Protocol-vid=34853&disposition=attachment&op=download.pdf
Towards a New WHOIS
- community.icann.org/display/EWG/Expert+Working+Group+Home
- www.icann.org/en/system/files/files/final-report-06jun14-en.pdf
- www.icann.org/public-comments/rds-prelim-issue-2015-07-13-en
- community.icann.org/display/gTLDRDS/Next-Generation+gTLD+Registration+Directory+Services+to+Replace+Whois
- www.icann.org/en/system/files/files/rds-user-accreditation-rfi-10feb14-en.pdf