Covert Wardriving With WiGLE
by 0rbytal
Most hackers are very familiar with (and enjoy) wardriving.
For those unfamiliar, wardriving is a network-discovery process where the curious digital explorer searches for wireless network Access Points (APs) using a tool like Kismet, NetStumbler, Wellenreiter, ESSIDJack, Airodump-ng, or WiGLE: The Wireless Geographic Logging Engine.
Wardriving harkens back to a popular activity from the B.G. era (Before Google) called wardialing: a method of discovering modems through automated, sequential, or random dialing of phone numbers. Early wardriving involved having a buddy drive you around while you sat in the passenger seat searching for wireless APs. The aforementioned tools made it easier for explorers to "wardrive" by enabling NetStumbler on their laptop, then stowing it away in their backpack to remain inconspicuous. But with the ubiquity of smartphones today, now you will likely have no idea when people are wardriving.
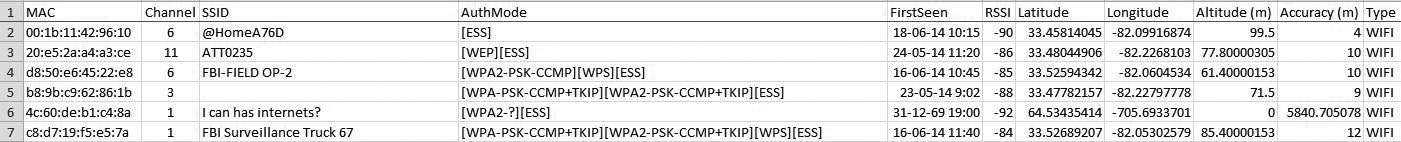
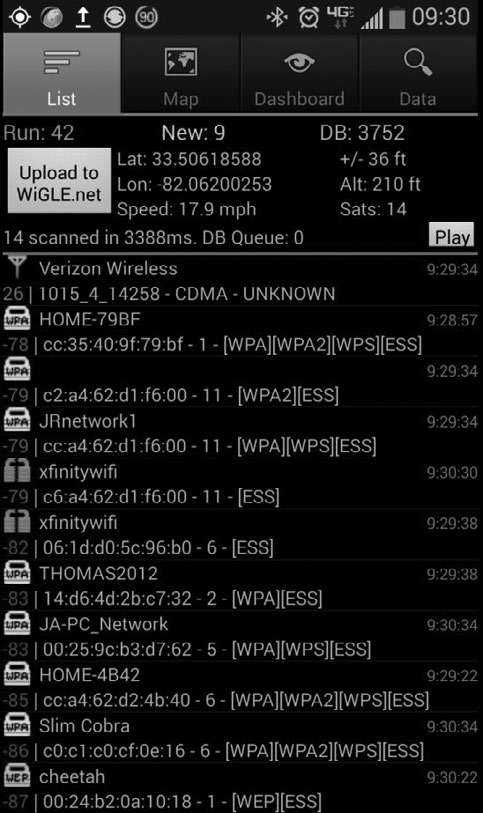
WiGLE has a fantastic app for Android called "WiGLE Wi-Fi Wardriving." After lacing up my running shoes for my weekly run, or whenever I'm driving somewhere new, I turn on my GPS and Wi-Fi, fire up WiGLE, press the menu button and select "Scan On" so I can begin logging every wireless AP it discovers along the route. At the end of my route, I press the menu button, then select "Scan Off" and export the run, pressing the "Data" tab and choosing "CSV Export Run." This exports the latest run to a Comma-Separated Value (CSV) file that can be viewed and modified in most spreadsheet applications.
Alternatively, at the end of your route you could press the "Upload to WiGLE.net" button and it will upload the latest run to wigle.net (using your username/password for the site - so, go sign up for an account first if you want to do this).
On the main screen (the "List" tab), the ESSID of each AP that is currently transmitting a beacon is displayed, along with its perceived received power (dBm) to indicate how far away it is (closer to zero means closer to you), and how the network is protected (e.g., WPA, WEP, Open). Also displayed is your current latitude and longitude measured by your device's GPS, the number of new APs discovered this run, and the total number of APs recorded in your database.
When you open the CSV file, the first row is merely the device information, so it's safe to delete the entire row. Reading your database (CSV) file in a spreadsheet application makes it easy to sort the data for target identification. The first thing I do when I open my file is custom sort by "Type" so I can remove all of the "CDMA" rows.
These are the cellular towers that WiGLE logs, and I don't have any use for them (yet). Removing them will leave only Wi-Fi APs that WiGLE has discovered, located, and recorded. Custom sorting the rest of the data by "AuthMode" will let you easily identify APs based on their protection. Seeing only "ESS" means it's an open network (no password required and no encryption).
"[WEP][ESS]" indicates the network uses only the Wired Equivalent Protection (WEP), which most hackers know can be cracked in just a few minutes using Aircrack-ng (as detailed later).
"WPS" indicates the AP has Wi-Fi Protected Setup (WPS), which can be brute-forced with Reaver. Surprisingly, out of the 10,393 APs recorded in my database, 944 are open networks (no security), 599 use WEP, and 5458 APs in my database use WPS. That means that 6904 APs (66 percent) of the networks I've discovered in my area would qualify as "low-hanging fruit" ripe for exploitation.
For the coders, a Python script (sidlog.py) developed by fellow r00tninja "blerbl" that records ESSIDs of discovered networks and client probe requests can be found at pastebin.com/KdDpnpva.
This script only works on a Linux machine with Scapy installed, and does not accomplish nearly as much as WiGLE. However, for the creative minds that are fluent in Python, it provides a starting point to develop your own application that could do things overlooked in all of the popular apps. One thing the sidlog.py script does that WiGLE doesn't do is log the probe requests of devices trying to connect to hidden networks. This script could be used in the recon phase before setting up airbase-ng with Hyperfox to perform a deviously effective "man-in-the-middle" attack.
If you (or your friend/family member) have a WEP "protected" network, you should change your wireless security to WPA2 using a long, difficult Pre-Shared Key (PSK), a.k.a. passphrase or password, and disable WPS. Why? Because WEP-protected networks can be cracked in less than ten minutes using just six simple steps.
Note: I'm assuming you are using Kali Linux, BackTrack 5 R3, or another Debian-based Linux distro, and your wireless card can be placed into monitor/promiscuous mode. If you don't already have Terminator installed, type sudo apt-get install terminator in the command line. It will make following these steps easier. I also assume you've already navigated to the directory where you want to save your packet captures to crack. (Type cd /root; mkdir scans; cd scans)
Step 1: Put your wireless interface (wlan1) into monitor mode and change the MAC address:
Step 2: Find a WEP-protected wireless network:
Find a network with "WEP" under the "ENC" column, copy the BSSID MAC address and note the channel number - these are both used in the next command. Once you've identified your target WEP AP, press Ctrl+C to stop the current Airodump.
Step 3: Identify an associated client you can spoof/deauthenticate.
Right-click in your Terminator window and select "Split Horizontally" to open a new terminal frame to use in this step. You will leave the packet capture running.
If a client pops up with a different MAC address under the "STATION" column, copy that MAC address for use in the following commands. Assume here that 55:44:33:22:11:00 is the spoofed/associated MAC address.
Step 4: Begin fake-authentication:
Step 5: Use ARP-replay attack.
Right-click in your Terminator window and select "Split Horizontally" to open a new terminal frame for this step.
Step 6: Aircrack the WEP packet capture.
Right-click in your Terminator window and select "Split Vertically" to open a new terminal frame for this step.
These six steps should generate traffic on the WEP-protected network using fake authentication (spoofed as a connected device) in order to capture an increasing number of initialization vectors that are used to crack the WEP key. Depending on the distance from the AP and the amount of traffic on the network, one can crack a WEP key as quickly as five minutes (or less).
Why should you care about your network being susceptible to attack?
Because once a malicious intruder is inside your network, they could exploit one of your connected devices, or connect their own device (e.g., a small Raspberry Pi) to your network and use it as a pivot. This technique would allow all of their Internet traffic to look like it is coming from your network!
I hope everyone now recognizes how susceptible WEP is to attack and chooses to only use WPA2 with a very long, difficult-to-guess/brute-force passphrase: !<32600m@g@z!/\/3
Secure your network, and explain to your neighbors why they should secure theirs. Download the WiGLE app for your tablet or smartphone and try it out.
If you're like me, you'll likely find yourself intentionally taking the long way home just to do more wardriving.
Hack all the things!