Google's Two-Factor Authentication: The Sneaky Trust Feature
by Samuel A. Bancroft (SamuelBancroft@gmx.com)
Since September 2010, Google has provided its users with the option to use two-factor authentication to add a layer of security to their accounts.
ATM machines are widely used as an example of two-factor authentication. The user has to provide a PIN number - something they know - and a debit card - something they have - in order to be able to gain access to their account. Having only one of the two factors would not be enough to satisfy the requirement to gain entry.
In the case of Google's two-factor authentication, Google uses their Google Authenticator phone and tablet app to create the second verification factor. But note, the user may use another application to generate the second verification if they so choose to.3 Google Authenticator is capable of using both the HOTP and TOTP algorithms to generate six integers that the user then uses to authenticate themselves.1,2 The TOTP, or Time-based One-Time Password algorithm uses a cryptographic key and the network's time to generate a new and unique six digit passcode every thirty seconds. For a user to be able to access their Google account, the user would in turn have to provide their password and also the unique six digit passcode, generated on their phone or tablet. Knowing the password alone would not suffice. This makes stealing the user's password useless unless the TOTP passcode for that specific moment in time can be derived or stolen.
On a side note, Google allows the printing of a special set of static passcodes in case the user loses access to the Google Authenticator app, i.e., if they lose the phone or tablet which they were using to generate the TOTP passcodes. These static codes are usually kept in the user's wallet.
But this article is not about how two-factor authentication works or how to beat it. Instead, this article will touch upon a feature Google is currently using that has the possibility of leaving the user open to an attack without them realizing it.
Google, in their efforts to make two-factor authorization less intrusive to the user, has implemented a feature that I have dubbed as the "sneaky trust feature."
When Google notices that a specific computer is constantly being used by the user to login, the two-factor authentication code page will automatically check the "Don't ask for codes again on this computer" check-box by default. Consequently, if the user enters their six-digit code and logs in without noticing the check-box or forgetting it's checked, the two-factor authentication for that specific computer is turned off without any notification to the user. Furthermore, this checked check-box is persistent. It will be checked every time the user attempts to login regardless if they have unchecked the check-box in the past.
The lack of notification creates a situation where the user may be unaware that they inadvertently trusted the computer. This in turn would give an attacker a window to use the newly trusted computer to gain access to the user's account without worrying about two-factor authentication. This attack window will likely be closed the next time the user logs in since they ought to notice that the TOTP passcode are no longer being asked for. Keep in mind also, since the user thinks they are protected by two-factor authentication, they may become more relaxed as to logging into their account from questionable computers, making stealing their passwords easier.
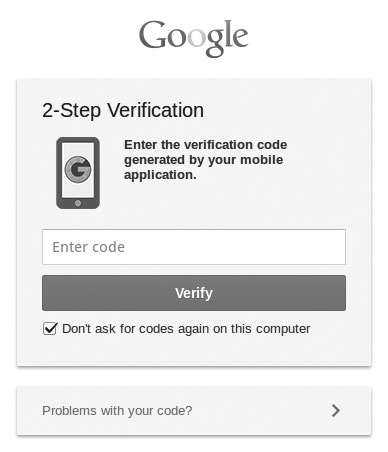
An example of the "Don't ask for the codes again on this computer" being checked by default.
The only notification is the small check-box being checked.
I installed Linux on a machine to test how often a user has to login in order for the "Don't ask for codes again on this computer" check-box to be checked by default. I found that after logging in 22 times within a time span of 23 hours, the check-box became checked persistently.
In order to clear the check-box from being checked, the user has to clear their cookies.