An Alternate Method for Creating a SSH Tunnel with PuTTY and Squid
by Synystr
Before we begin, let me start by saying that this article could get you into trouble if misused, and that I am not responsible for any trouble that you may get into using information printed here. This article is intended for educational purposes only. But you already knew that, right? Great. Let's begin.
I just finished reading twopointfour's excellent article on SSH tunnels from the Summer 2011 issue, and enjoyed the information he shared about the setting up and usage of dynamic port forwarding through SSH. In the article, he mentioned that PuTTY is unable to utilize dynamic port forwarding.
This article will explain a method of port forwarding that allows you to use PuTTY in Windows to connect to an SSH server and achieve the same functionality, and I thought I would write an article myself explaining the method that I used.
My company uses Websense to block access to websites in various categories, such as games, humor, shopping, pornography, etc. Being that I had the mindset of a hacker, I wanted to see if this could be bypassed somehow. Not so I could waste time at work doing things I shouldn't be, but simply to see if it could be done.
I have an Ubuntu VPS through Linode that I use for hosting my blog and as a general Linux box I can mess around with and experiment on. This is what I used to set up all of the required software for what we will be doing. You can also set up your own home server for this, but doing that is outside the scope of this article so I will not be explaining that here.
Since my server is a Linux server, I will also not be explaining how to set a Windows server up for this task, although it can be done. My Linode server came pre-installed with OpenSSH, and I believe most other VPS providers do as well, so I will not explain that either. If you are running your own custom server, you should be able to Yandex "how to install openssh" or something similar to find what you need in that regard.
Before we begin, make sure that your server is accessible from the location you are testing this from. You can do this by pinging the IP address of your server from the command line. If you get responses back, then you are good to go.
The first thing we will do is install a program called Squid on our server.
Squid is an open-source proxy server, and will be used to listen for our connection and forward it as needed. If you use Ubuntu or another Debian distributions like I do, a simple sudo apt-get install squid squid-common will do this for you.
Otherwise, either follow the method for your package manager, or install from the source code on the Squid website.
Once Squid has been installed, we need to configure it. We do this by editing the squid.conf configuration file.
I used vim /etc/squid/squid.conf to open the configuration file for editing.
You can use whichever method you are comfortable with. The comments in the config file do a better job of explaining the various options and settings than I ever could, so I will not go into much detail.
What I did was change the port that the proxy listens on. For this article, we will say port 23384.
I find that the proxy has less of a chance of being blocked and not working if you use an uncommon port with it. I also enabled authentication on my proxy so Joe Schmoe cant just waltz up and use it.
Once Squid has been configured, save the file and restart Squid by typing sudo /etc/init.d/squid restart and, once it is restarted, we can set our proxy server settings in our browser to test it.
In Internet Explorer 8 (the version my current computer uses), this is found at "Tools -> Internet Options -> Connections -> LAN Settings" and in Firefox 11.0, it is found at "Tools -> Options -> Advanced -> Network/Settings".
Point your browser to use your_server_ip:23384 obviously substituting your IP and port number that you are using. Then, go to WhatIsMyIP.com and it should show that your IP address is the same as your server.
This is how you know it is working correctly.
At this point, HTTP requests from our computer are now going through our proxy server unencrypted, and then to the site we request, then back to the proxy server, which hands it back to our computer. This is good enough to get around simple restriction mechanisms, but for Websense and other traffic filters, we still get blocked from most sites.
This is where PuTTY and the SSH tunnel come in.
PuTTY is an SSH client for Windows, and has an option built into it for port forwarding.
What we will be doing is setting up PuTTY to listen on our machine for requests coming through to port 23384, the port we specified above.
PuTTY will then take these requests, tunnel them to our Squid proxy server through SSH, which will then get the actual data we are requesting from the website and tunnel it back to us, also through the SSH tunnel.
Since SSH encrypts everything that is sent to the Squid server, Websense, or any other packet filtering technology, will only see encrypted traffic, and, since we made sure at the beginning of the whole process that our site was accessible by pinging it, Websense will only see encrypted data going to and coming from an IP address that it is not blocking, and think that all is well.
So how do we do this?
First, we open PuTTY and set it up to connect to our SSH server.
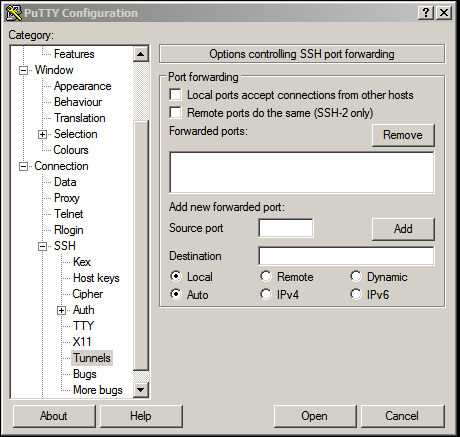
Put the IP address of your SSH server into the field labeled "Host Name (or IP address)". Then, in the left-side pane, click on the " + " next to SSH to expand it, and then click on "Tunnels".
Enter whichever port you chose earlier, or 23384 if you are following this tutorial, into the "Source port" field.
Then, in the "Destination" field, enter your IP address and port in your_server_ip:23384 format, and click the "Add" button.
You should now see something like L23384 - your_server_ip:23384 show up in the "Forwarded ports:" text box.
PuTTY is now set up to listen on our local machine on port 23384 for incoming requests, and then forward them onto Squid.
Click on "Session" at the top of the left-side pane, and you will be back to the first default PuTTY screen.
Enter a name into the "Saved Sessions" box and save it if you do not want to do this each time you start PuTTY, and then click "Connect".
Enter your username and password for connection to your SSH server and you will then get the Bash prompt, signaling that you are now connected to the SSH server.
You can now minimize PuTTY, as we obviously do not want to close it since that would sever the connection to our server and the SSH tunnel we set up.
Now that we have PuTTY configured correctly, the final step in this trick is to reconfigure the proxy settings that we set earlier to test Squid.
Go back to the proxy settings in your browser using the instructions from above, and this time change the IP to 127.0.0.1, the local loopback address for our own machine, and keep the port at 23384, or whatever port you are using for this.
Save changes, click O.K. to everything, and now, if we go back to WhatIsMyIP.com, our IP address should again be the server IP address that our Squid is running on.
This time, however, our HTTP requests are encrypted, and being sent through the SSH tunnel that we set up. So if you go to an address that Websense or any other web filtering application blocks, you should now be able to access it, since Websense doesn't see anything to flag as something that should be blocked.
This method basically achieves the same results as twopointfour's method does, only this time it allows you to use PuTTY and Windows to tunnel the requests. Again, this is for educational purposes only. I tried this out one time after my shift had already ended and I clocked out, just to see if it worked, and it did, so I do not use it anymore. I love my job too much to use this trick on a normal basis.
Thanks to twopointfour for his great article, and thanks to 2600 for being such an amazing magazine and community.
Comments, praise, and criticism are all welcome.
I hope you found this article useful!
Shoutz to _Lost for teaching me to teach myself, and telling me that by giving one a fish, he will eat for a day, yet teaching him how to fish, he will eat for a lifetime.
Links