Simplex Locks: Illusion of Security - Version 2.0
by Beyond
In the Autumn 1991 edition of 2600, Scott Skinner and Evil Corley detailed how to brute force Simplex locks in an article titled "Simplex Locks: Illusion of Security."
The article even featured an accompanying list of groups of codes that one could use to brute force one of these locks open. They were able to run through the entire list of codes at ten minutes on average.
For those not keeping score at home, that means an open lock in no more than the ten minute average.
While this technique still works, a once closely guarded technique has emerged publicly and in the form of a class action lawsuit against KABA-Ilco, the manufacturer of the Simplex line. Certain models under the Simplex line (detailed below) can be bypassed in seconds when a rare-earth magnet is strategically placed on the lock.
If you don't know what we're talking about, image search "Simplex 1000" on your browser of choice. The Simplex 1000 is arguably the most popular Simplex model, along with its lever variant the L1000. You've undoubtedly seen them everywhere. I'm not here to argue who is in the right and who is in the wrong, or what measures should be taken in this situation.
I'd much rather inform you of this bypass and applicable information. With that said, I do want to note that KABA-Ilco has always marketed the Simplex line as a convenience lock and not as high-security.
A class action lawsuit was filed against KABA-Ilco regarding this bypass in November of 2010.
The lawsuit stipulates that KABA-Ilco knew of the bypass and did nothing to correct it. KABA-Ilco contends that locks manufactured after September 19, 2010 are not susceptible to this bypass, although I've heard from reliable sources that this is simply not the case.
First-hand accounts suggest that this bypass technique was taught as early as 2000, or perhaps 2001. I recall a company even selling a magnet intended to bypass these locks around 2003, a fact I shared with one of the lead plaintiffs in the case earlier this year.
How exactly does this bypass work?
I could fill almost an entire edition of 2600 detailing exactly how the bypass works but I think, for the sake of brevity, you should read the most detailed explanation from Marc Weber Tobias on his blog: www.thesidebar.org/insecurity/?p=761
Long-story short, a well-placed, rare-earth magnet with substantial pulling force can pull an armature inside the combination chamber away from its intended position which puts the combination chamber in an unlocked position, thus unlocking the lock when the outside lever or knob is turned.
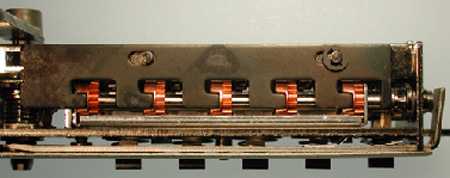
This is the combination chamber for a Simplex 1000 lock manufactured prior to September 19, 2010
A critical component can be moved with a strong magnetic field.
When viewing the lock head-on, the magnet should be placed on the left side of the lock with its center around 1-1/8" below the center of the last button, which is a 5.
If placed correctly, the knob or lever will retract the lock's latch.
Neodymium disc magnets, 3" x 1" at N52 or N54 ratings, with a pull force of between at least 400+ pounds represent the minimum capable of allowing this bypass to occur.
A stronger pull force will definitely work, but you're going to be paying for that added strength. These magnets can be purchased at Applied Magnets.
Heads up, they are expensive and can be very dangerous if not handled properly. Brush up on magnet safety if you intend to play around with this bypass.
Which models under the Simplex line are vulnerable to this bypass?
Any model that uses their M-56 or M-63 combination chamber, or variant, is susceptible to this bypass.
These models include, as identified in the lawsuit, the 1000 (and its variants), 2000, 3000, 6000, 7000 (easiest to bypass), and 9000 series, which all utilize roughly the same combination chamber.
The 7000 series is the easiest because it features the smallest "air gap" between the combination chamber and the outside of the lock.
Does this attack always work? No.
Certain models under the Simplex line feature a totally different combination chamber, such as the LD450/LD470 series.
The 900 series, for example, features the combination chamber on the inside of the door.
The lock's mounting on a door can also prevent successful magnet placement, such as the door jamb to the left of the lock which will rarely provide enough room to accommodate one of these magnets.
Digital retrofit kits are also marketed that replace the traditional combination chamber with an electronic version featuring a solenoid, which could potentially be bypassed with a magnet, but that's for another article.
It should be noted that the digital combination chamber is not susceptible to this exact bypass. Nevertheless, in their 30 plus years of existence, there are millions of locks in use that do allow for the bypass given the right circumstances.
While the "magnet bypass" offers quick entry, the brute-force method as identified by Skinner and Goldstein in 1991 represents probably the most reliable, but not necessarily the quickest, method for bypassing these locks.
There are certainly other methods, but given a few subjective criteria, such as lock placement and surrounding hardware, the brute-force method will always work when time is available.
I'll end with a piece of information shared in the original article that still rings true today: before trying anything, test for the default code of 2 and 4 pressed together and then 3.
If this is the correct code, turning the knob or lever will retract the latch and allow entry.
To quote Skinner and Goldstein, "It is always good to take a few lucky shots before you initiate a brute-force hack."
