Vulnerabilities in Quantum Computers
by Purkey
First of all, what is a quantum computer and how is it different from current computers?
Current computers operate on bits, as everyone knows. You can think of bits as a bunch of light switches that are either on or off.
A quantum computer is different in that the light switches can be on and off at the same time. Furthermore, the toggling of one switch may change another - this is known as entanglement.
So a quantum computer has a bunch of these switches, which are called qubits, and each qubit can be in multiple states at once until it is measured. At that point it becomes a specific value, just like a regular computer, but this value is randomly selected from the possibilities.
So why are quantum computers useful?
The big reason is that quantum computers can efficiently factor. Given three and five it is easy to know they multiply together to be 15, but given 15 it is much harder to know that it is the product of three and five.
This "one way" problem forms the basis of many modern encryption systems, SSL included. But because the result of the quantum computation is random, you may have to try a couple of times to get the right answer.
So if you have a quantum computer, you can decrypt most of the encrypted communications over the Internet. Obviously, this is something that most governments would want to get their hands on.
While this all sounds great, quantum computers are still a number of years off - the best guess is 2021, plus or minus five years.
There are some that exist in labs, but only with a handful of qubits. So building quantum computers is a very hard problem. When they finally do arrive, it will be much like computers were in the early days - expensive and shared by many users.
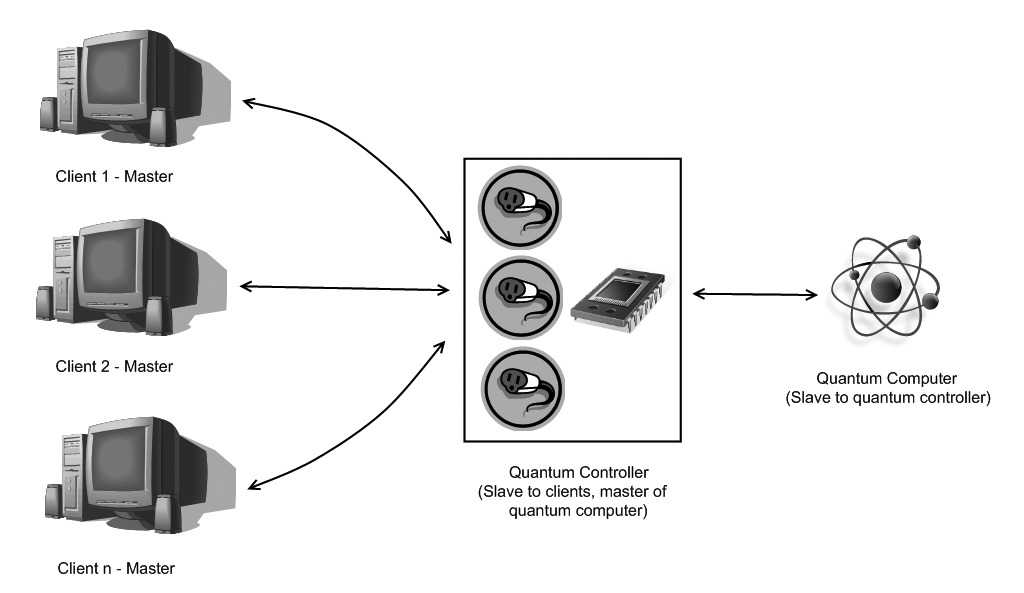
The currently proposed architecture is called a Quantum Random Access Machine, or QRAM for short.
In this architecture, an existing computer communicates with the quantum computer, sending commands and receiving results. This can easily be shared, even over the Internet perhaps.
As one can imagine, there are a number of ways this architecture can be exploited.
The most apparent way would be a "man-in-the-middle" attack. Since the results are random, you could consistently give the wrong answer.
Or, if you wanted to see the results, perhaps of decrypted communications, you could just watch the traffic.
If the quantum computer is shared over the Internet, you could also break in and utilize it for your own purposes.
Since the first quantum computers will likely be owned by governments or large corporations, this may be the only way we'll get to play with them...