CrazyGeorge - Security Through Obscurity
by Lnkd.com?2600
Around 7:30 pm on August 4, 2009, George Sodini, a .NET software developer living only a few miles from myself, walked into a fitness center in a local strip mall where about two dozen women were taking a "Latin Impact" class, took some guns out of his gym bag, turned off the lights, and opened fire on the women, killing three of them and injuring a number of others before shooting himself (en.Wikipedia.org/wiki/2009_Collier_Township_shooting).
He had been blogging about his "exit strategy" for nine months, starting the day after the 2008 election, including an aborted attempt on January 6, 2009:
"It is 6:40pm, about hour and a half to go. God have mercy. I wish life could be better for all and the crazy world can somehow run smoother. I wish I had answers. Bye."
"It is 8:45PM: I chickened out! Shit! I brought the loaded guns, everything. Hell!"
Access to the blog was protected with a simple "password" scheme that constructed the address of the target page by inserting whatever the user entered as the password into the next location's URL. If you entered the right password, up popped one of the other pages on the site. If it was the wrong password, a customized 404 error page was displayed saying, "Sorry, the page you were looking for could not be found."
With a little cleaning up, the script that used on the GeorgeSodini.com web site looked like this:
<html> <head> <script language="javascript" type="text/javascript"> function password (pass) { if (pass != '') { location.href=pass+".html"; } } </script> </head> ... |
This simply loads another page in the same directory into the browser.
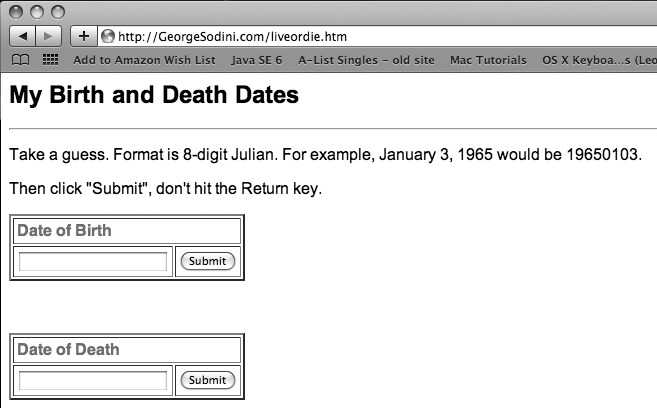
A page named "liveordie' was linked from "Life or Death" on the site's home page.1 It included a single form with two input fields:
<p>Take a guess. Format is an 8-digit yyyymmdd date. For example, January 3, 1965 would be 19650103. Then click "Submit", don't hit the Return key.</p> <form name="login"> <table border="2" cellpadding="3"> <tr><td colspan="2"><b>Date of Birth</b> </td></tr> <tr><td><input name="pass" type="password"></td> <td><input type="button" value="Submit" onClick="password(form.pass.value)"></td> </tr> </table> <table border=2 cellpadding="3"> <tr><td colspan="2"><b>Date of Death</b> </td></tr> <tr><td><input name="pass2" type="password"></td> <td><input type="button" value="Submit" onClick="password(form.pass2.value)"></td> </td> </table> </form> |
While one input field would be sufficient to handle multiple passwords, having both allowed displaying the text that provided the clues to what page names needed to be entered. The password that worked during most of the nine months the blog was being created was probably 19600930, the "Date of Birth," since even George would not have known that the the "big day" was going to be 20090804 until the day before. It's likely that the blog page was renamed when George's decision changed from "live" to "die."
While in this case only one of the two clues led to a page that existed, which makes sense for a running blog, you could use the same principle for hiding any number of pages. You could request the user to enter a "keyword," and set it up so that each valid keyword directs the user to a different hidden page. To ensure they don't get cached by search engines, I would suggest adding a meta tag to the head section of the target pages:
<meta name="robots" content="noarchive"> |
The CrazyGeorge.com web site (which simply framed pages at home.comcast.net/~space777) had two levels of hidden pages. The first level used a slightly different version of similar code (again, cleaned up a bit):
<html> <head> <script language="javascript" type="text/javascript"> function password (pass) { if (pass != '') { location.href="/"+pass+"/index.html"; } } </script> </head> ... |
Putting the "password" in the path part of the URL effectively hides all of the files in a directory behind the same password.
Once you were past that, using the password crazyg, there was a framed navigation bar with a variety of links. he link labeled "Private" took you another password entry form for access to hidden pages in the home.comcast.net/~space777/crazyg/personal directory. As of this writing, I don't think anyone has gotten past that level yet.2
One unique aspect of this technique is that the only place the password appears on the server is in its file system. You could have full access to the source code of the web pages and still be unable to discover the password to the HTML pages and other files. For example, you could create a picture gallery where the HTML page(s) and all the pictures were protected.
Contrast this with other places where you can get the image names from their src attributes in the HTML and bring up the images completely unprotected.
One disadvantage to this method, especially if you're trying to make your web site or blog infamous, is that the hidden pages won't get indexed by search engines or web archive sites, unless you manually submit specific pages yourself. Once the domain name expires, that might be the only place the content of the web page survives.
So George, wherever you are, when you said "my voice will speak forever!**" in your blog, most people will probably forget about the incident in a short while, but a few snippets of your JavaScript code will survive a bit longer on these pages.
Footnotes
1.) While everyone was focusing on the blog page itself, in my opinion the "Life or Death" question, and how the blog page was renamed when the decision was made, was significant also. Wikipedians must not have agreed, though, because the few sentences I added were deleted. Hopefully this article provides some insight into both the dark side of human nature and a simple security technique.
2.) I did check the source code to see if there were any clues to the password. On one of his other sites the source code said to e-mail him for the password, and I checked for an autoresponder, but there wasn't one - George would have had to be there. A dictionary attack didn't work and neither did passwords for other pages, keywords from the text, his girlfriend's first and/or last name, or his cat's name "snippers," which was a test password commented out in the source code.
If anyone does manage to get past the second level of security on the CrazyGeorge.com site to access the "darker side must be hidden" page(s), I'll post what we find at 216.69.163.48/crazyg.
If that page still says the page could not be found and someone else discovers the password to get to the .../crazyg/personal/... pages, please let me know by contacting me at Lnkd.com?2600.