Microsoft, Please Salt My Hash!
by Sam Bowne
The excellent book Hacking Exposed, Sixth Edition, by Stuart McClure, Joel Scambray, and George Kurtz, contains this terrifying statement: "All Windows hashes suffer from an additional weakness: no salt" (from page 184).
Is it possible that Microsoft made such a stupid, irresponsible error? Sadly, they did, as I will explain and demonstrate.
Cleartext Password Storage
When you type in a password to log in, the operating system compares your input to a stored password. If the password is stored in a file, as shown in Table One, an attacker can steal that file to learn all the passwords - a very insecure system.
Table One: Cleartext Password Storage
Username Password Administrator zaphod Amir opensesame Joe password Lucretia password |
Password hashes
Hashes make stored passwords safer. A "hash" is a way to scramble data, designed so that it is easy to calculate, but very difficult to reverse. One popular hash function is MD5, which you can calculate online at this website: md5-hash-online.waraxe.us
Now the stored file contains hashes, as shown in Table Two, instead of cleartext passwords. When you log in, the operating system calculates the hash of your input and compares it to the stored hash.
Table Two: Hashed Password Storage
Username Password Hash Administrator c953ef6978d4525b35620e9f70234aa9 Amir e6078b9b1aac915d11b9fd59791030bf Joe 5f4dcc3b5aa765d61d8327deb882cf99 Lucretia 5f4dcc3b5aa765d61d8327deb882cf99 |
If an attacker steals the hashed passwords, he or she must reverse them to retrieve the original passwords. But there's a weakness in this system. Compare the hashed passwords for "Joe" and "Lucretia" - since they both have the same password of "password", the hash is the same. That's not safe! An attacker could pre-calculate the hashes of many common passwords and use that table to recover the passwords.
What is a Salt?
To make hashes safer, random "salt" values are appended to the password before hashing it, as shown in Table Three. The salt is then stored with the hash value, as shown in Table Four. When you log in, the operating system appends the salt to your input, calculates the hash, and compares it to the stored salted hash.
Even though "Joe" and "Lucretia" have the same password, there is no easy way to know that from the salted hashes. Attackers can't make a dictionary of password hashes now, unless they make thousands of dictionaries, one for each possible salt value.
How Does Windows Store Passwords?
To find out, I made the accounts shown above on a Windows 7 (Beta) machine.
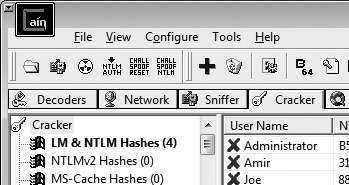
Then I used the free program "Cain" from oxid.it/cain.html to dump the hashes. To do that, just click on the "Cracker" tab, right-click the center of the window, and click "Add to list". Then click "Next". As you can see in Figure One, the hashed values are the same for "Joe" and "Lucretia". I tested this on Windows 7 (32-bit), Windows Vista Business (32-bit), Windows XP Professional (32-bit), and Windows 2000 Professional, and the hash for "password" was identical in all cases. I also confirmed that the hash is the same for a local account on a Windows 2008 Server Datacenter 64-bit machine, using fgdump to gather the hashes.
Table Three: Salting and Hashing Passwords
Username Password Salt Password+Salt Hashed Password+Salt Administrator zaphod WM zaphodWM 759e9786a86814820d19a8d4b642443a Amir opensesame 45 opensesame45 c559d397235a44bf906d4f86cdd3e1a9 Joe password q2 passwordq2 984e1b8949abbd846399e38d0f2cae81 Lucretia password 2r password2r 55d1776bb284bbba75ddb31e3480b000 |
Table Four: Salted and Hashed Password Storage
Username Salt:Salted Password Hash Administrator WM:759e9786a86814820d19a8d4b642443a Amir 45:c559d397235a44bf906d4f86cdd3e1a9 Joe q2:984e1b8949abbd846399e38d0f2cae81 Lucretia 2r:55d1776bb284bbba75ddb31e3480b000 |
Conclusion
The statement in the Hacking Exposed book is correct: Windows does not salt its password hashes.
This is a shameful security error on Microsoft's part, and needs to be corrected. The UNIX crypt() man page says this feature has been included in UNIX since versions 6 & 7 of AT&T UNIX, which came out in 1975 and 1979. How can Microsoft continue to use a system which has been obsolete for 30 years?
We, the consumers, need to demand more. I hope that this article may help to shame Microsoft into doing better work.
About the Author
Sam Bowne teaches Ethical Hacking and other classes in the Computer Networking and Information Technology department at City College San Francisco.
His website is samsclass.info.