Fun With the Snom Outlook Add-On
by reid
VoIP security is a growing field.
In a previous article, I gave a brief overview of some attacks on VoIP systems. In this article, we'll take a look at a specific piece of software that allows calls from a Snom IP phone to be initiated remotely using an add-on for Microsoft Outlook.
For the techniques described in this article, you'll need four things: access to a network which uses Snom IP phones, IP phones with the HTTP server enabled (which is the default setting), Microsoft Outlook, and Snom Outlook Add-In.
You can download the add-in from: www.snom.com/download/share/snom-Outlook-Addin.zip
You can also find some screenshots and configuration guidelines at wiki.snom.com/Outlook_Add_In.
I did my tests on Microsoft Outlook 2003, but I have every reason to believe the 2007 edition would also work.
Snom is a German manufacturer of business IP phones.
The Snom Outlook Add-In allows users to call contacts from Outlook using their phones.
Pretty simple, right?
Well, the way it does this is by sending a specially-crafted HTTP request to the built-in HTTP server on the phone itself.
The only authentication that is used to determine that the Outlook user is the actual user of that phone is that you input the IP address of the phone into the configuration screen in Outlook. Nice, right?
It implements the remote call initiation by sending a simple GET request like:
GET /index.htm?number=1234567890 |
So, if you can craft an HTTP GET request, then you can think of all sorts of much more efficient ways to use this feature, but again people, explore, don't destroy, mmmmkay?
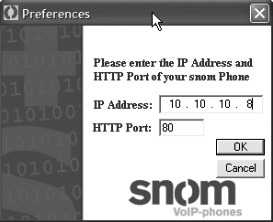
The obvious hilarity ensues if I sit on a network where I know Snom phones exist in the IP address range of: 10.10.10.0/24
Then, I can pick an IP address in that range and enter it into the configuration screen shown below.
The default web server port is of course 80, but maybe you use some other port for HTTP; if so, just change the setting. This does not work using HTTPS.
Once configured, I select a contact from my Outlook contacts and click on Call Contact from the new menu which the Snom add-on created.
Once that button is clicked, a call is initiated to the number stored for that Outlook contact from the IP phone at the address configured. Since no authorization is implemented, the call goes through as long as the IP address is valid.
Suppose that Bob uses a Snom phone at work.
Maybe Bob just happens to know that the IP address of his CEO is: 10.10.10.8
If not, Bob has the option of running a quick Nmap scan; he might get back information like the following:
C:\> nmap 10.10.10.0/24 Interesting ports on Jim-snom. mycompany.net (10.10.10.110): Not shown: 1678 closed ports PORT STATE SERVICE 80/tcp open http 443/tcp open https |
Bob now knows that Jim the sales-weasel has an IP address of: 10.10.10.110
Bob pops the IP address of Jim's phone into the add-in and has it call random customers or, even better, random irate customers.
Here's the impact: when Bob clicks on Call Contact from the Outlook menu, three things happen.
First, Jim's phone rings.
Second, the number for the selected Outlook contact rings - even if Jim doesn't pick up his phone.
If the called party picks up first, the call is still connected to Jim's phone.
Third, a webpage pops up on Bob's laptop that displays the status of Jim's phone.
The webpage opens independently from the call being completed; as long as the HTTP request goes through to the phone, a web page pops up.
Now, perhaps you're wondering if this piece of software is really necessary. Of course it's not.
Bob can just as easily login to the phone itself via http://[IP Address] and plug in the phone number to call manually.
Alternately, Bob can just craft the request and send that off. Again, there are lots of possibilities.
When the call is placed, Jim's phone rings; when he answers, the call is connected to whatever contact Bob clicked on. The resulting conversations can be interesting:
Alice: "Hello."
Jim: "Hello."
(This goes back and forth a few times before Alice checks her caller ID to see what crackhead she's talking to.)
Alice: "Oh, Jim, it's you. Hi, I'm glad you called; I've got some billing issues that need to be cleared up."
Jim: "Okay, happy to help, but I'm a bit confused. You called me."
Alice: "Hang on a sec Jim, let me get my bill, but no, you called me."
And, of course, hilarity ensues.
There are of course some limitations and other caveats to this.
If the SIP account tied to the phone has account codes or toll barring enabled on it, then calls may not complete.
Another good example is to call a 1-900 number or any IVR system.
Suppose that you have Jim's phone call 888-423-8726.
This is the support number for Adtran, a well known telco equipment vendor, where an IVR system automatically answers the call.
Jim's phone doesn't even ring; it just suddenly starts talking to him.
Again, hilarity ensues. As long as the number dialed is within the allowed dial plan for the phone, the call complete - be it the receptionist at the front desk, 911, whatever.
I'm going to stop giving you ideas now...
Another interesting way to utilize this is in conjunction with the Snom DND or "Do Not Disturb" feature.
If a phone has the DND feature activated, calls will immediately go to voicemail.
Now, suppose that Bob sets up his voicemail with an outgoing message that's 0 seconds in length.
When a call goes to voicemail, all the caller will hear is a short beep before it begins recording.
So, if Bob sets his phone into DND mode then has Jim call the phone, it immediately goes to voicemail and begins recording anything Jim says using the speakerphone built into the casing of the Snom phone.
In this way, Bob can record anything that Jim says.
The only indication of this is a short beep before the voicemail begins recording.
This is, of course, just one option. Creative thinkers will also imagine what happens when Jim's phone is set to call a rotary group pilot number.
This type of remote call initiation isn't anything new.
There are a number of VoIP phones with HTTP servers built in which allow you to dial from your phone's web page.
You can do all sorts of creative things with this, but this is simply one example where a piece of software can entertain and annoy with point-and-click ease.
As many readers will immediately realize, the simplicity of initiating calls via a basic HTTP GET request also means this setup is vulnerable to scripting; a simple shell script to loop through subnet ranges initiating calls would be a relatively straightforward task.
I'm not going to show it here, but I have verified that it works just fine.