Zero-Knowledge Intrusion
by S. Pidgorny
This article is about evasion of Intrusion Detection Systems (IDS): whoever monitors activities on the target network should have zero knowledge about these activities.
Before continuing, I must warn that unauthorized access to information systems is crime in most countries. The point of this write-up is awareness of the possibilities, which will help protecting infrastructure.
Zero-knowledge intrusion is based on two principles: perform only passive reconnaissance, and do not ever generate traffic that is not generated by legitimate clients on the network.
Intrusion detection systems are based on anomaly detection. You just don't create anomalies.
Why this is better that just locating an available port or disconnecting the victim system?
Because it doesn't create anomalies: there are no new connections to the port on the LAN switch, and only temporary disconnections of existing systems. As such, alarms probably won't be raised.
Of course, you need to power the intrusion agent using some kind of power source, and hide it but modern office buildings seem to be designed for just that. Audits of power-consuming devices are unheard of. Entering the building is beyond the scope of this article; I refer you to (((Hollywood))) movies for ideas.
A very important aspect is remote control of the intrusion agent.
My preferred way is to use mobile data services available on commercial GSM and CDMA networks. This is better than Wi-Fi because companies sometimes employ specialized "wireless" intrusion detection systems which focus on detecting the presence of alien Wi-Fi devices on premises. There is also the ability to control the agent from pretty much anywhere in the world. A dial-in IP connection to the agent is one option. A better approach is to connect the agent to an intermediary server and go through that.
Start the reconnaissance without using an IP address. Make sure you don't assign an IP address and don't start a DHCP client on your Ethernet interface; use ifconfig eth0 up to activate the interface.
This is sufficient for running tcpdump or another traffic sniffer. You have to capture traffic for a few days and analyze the results. The information you're looking at includes, but isn't limited to, DHCP and DNS configuration, Windows infrastructure (such as names, domain controllers' locations), messaging infrastructure details, software distribution and active network monitoring tools. All traffic of the victim system will be available for sniffing, which helps greatly: on a stand-alone port, only broadcast-type information would be available.
The second stage of zero-knowledge intrusion involves IP connectivity and generating network traffic.
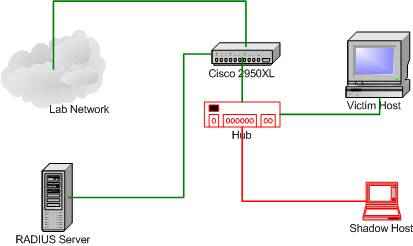
The way we connect to the victim network also helps here: it allows connecting to the IP network even if 802.1x port security or another endpoint security mechanism is used. The intrusion agent will have to have the same MAC address for the LAN connection as the victim host and have netfilter configured to deny all inbound connections. See Reference 1 for further details.
Cloning is a powerful technique and an important part of zero-knowledge intrusions. There's an interesting application for it which allows connecting to secured wireless networks.
Let's say the target organization deployed a WLAN according to Microsoft's secure WLAN deployment guidelines, using either PEAP and passwords or EAP-TLS and certificates for authentication (see References 2a and 2b).
Elements of the solutions include dual computer/user authentication, a RADIUS server with a TLS certificate, and strong traffic encryption with dynamic random keys. These components are all very secure unless you can clone an authorized client system.
Only opportunistic intruders steal documents and artifacts; those with a plan and determination make copies. Since the system that has been cloned is not stolen, alarms are not raised. Take a Windows laptop system image, install it on another laptop, change the local administrator password, change the AuthMode registry value (under HKLM\Software\Microsoft\EAPOL\Parameters\General\Global) to 2, and reboot.
Now the computer will authenticate with its own credentials, either password or certificate, and you are connected to the secure WLAN. That is another way of connecting the intrusion agent without physical intrusion or presence.
Now, when you have IP connectivity, the rule is not to use any type of network connection that is not used by legitimate clients, as seen in the information collected during the first stage of intrusion. This is very important.
There are many "ethical hacking" courses, and they pretty much all suggest using tools like Nmap (see Reference 3) for network mapping.
Don't use it - even with the paranoid timing option. The rationale is simple: if you run nmap -T Paranoid host.internal.example.com then some unusual connections will be attempted. Unusual is suspicious.
Intrusion detection systems may be configured with a rule that Echo service (on ports 7 TCP & UDP) is not to be used anywhere on the network. The Nmap run will trigger the alarm with a single packet.
However, NetBIOS over TCP/IP is considered normal on most networks, so you can sweep subnets using tools like NBTScan (see Reference 4) without triggering alarms, because connections on 137 (UDP) are "good."
In the end, you have a system that is connected to the network and knowledge about the normal behavior of network clients. This provides an ideal base for an active attack.
The zero-knowledge status will end at some stage. But by limiting the attack to the use of information obtained using social engineering elsewhere, the window of opportunity for attack can be greatly extended with specific weaknesses of the network in question and zero-day exploits against protocols that exist on the infrastructure.
Shouts out to the Coffee Company of Balaclava, hello to ES, and good luck to the P&A squad.
References
- Getting Around 802.1x Port-based Network Access Control Through Physical Insecurity
- Securing Wireless LANs with PEAP and Passwords v1.6
- Securing Wireless LANs with Certificate Services v1.6
- Nmap Free security scanner for network exploration and security audits.
- NetBIOS Name Network Scanner