Hacking Cisco IP Phones
by Moby Disk
This article pertains to the Cisco 7940 & 7960 IP phones.
For those new to IP phones, they function like normal office phones on a PBX but they run over Ethernet. This makes them highly hackable.
The Cisco phones have a monochrome pixel-addressable LCD display. They communicate via 10/100 Ethernet at full- or half-duplex. The firmware is updateable and Cisco provides firmware to support several voice protocols.
Power can be provided via AC or via unused wires on the Ethernet cable. The phones communicate with a call manager server that handles configuration, mailboxes, etc.
The phones support a wide variety of protocols. This article will use the main configuration protocols including Dynamic Host Configuration Protocol (DHCP), Trivial File Transfer Protocol (TFTP), and Telnet. Other supported protocols used include DNS, SNTP, and ICMP. Real-Time Transport Protocol (RTP) is used for audio (Ref. #3). Various protocols including SIP, MGCP, and SCCP are used for signaling other phones. HTTP is supported for downloading graphics to display on the LCD.
I looked into these phones first out of hacker curiosity: This is a great example of digital convergence.
I was amazed that these phones were actually computers and that I could communicate with them using my desktop PC. I also wanted to know how secure they were. Could someone listen in to calls? Fake calls? Make the phones randomly yell insults at coworkers? Well, I was surprised to find that Cisco didn't even put one bit of thought into security. It is trivial to do all of these things and more. Let's see how...
Required Tools
All you need to execute the basic hacks is access to the network that the phones reside on.
If your computers are on the same switch as the phones, you can just use your desktop PC. Otherwise, obtain a hub.
A plain Windows 2000 workstation includes the necessary Telnet and TFTP client. Some of the more advanced tricks require a TFTP server. If you do not have physical access to the phones themselves, you will need a sniffer to determine the IP addresses and names of the phones.
Security
The Cisco phones I used provide no security whatsoever.
Every employee necessarily has physical network access. A wireless router would allow anyone to remotely control your phones without physically being in the office. In this particular office, the phones were actually accessible from outside the office!
Once I had the IP addresses, I was able to Telnet to the phone on my desk from my home PC.
Newer versions of the Cisco CallManager software require digital signatures to make it more difficult to spoof firmware updates and also supports IPsec. If you do use an IP phone system, I strongly recommend using the latest software and enabling IPsec.
You should also configure the phones to disable Telnet access. This can be subverted by spoofing the TFTP server and sending fake configuration files, but that is much more difficult.
Hacking
So what exactly can be done remotely with these phones?
You can do anything available via the menus or buttons physically on the phone.
Remotely Change Phone Settings
- Change the ring tones (predefined tones or use your own).
- Modify the firmware.
- Change the logo on the display.
- Redirect the company directory or the voice mail.
Remotely Control Phones
- Initiate calls (with speakerphone).
- Make the phone ring.
- Adjust the volume.
- Take phone on/off the hook.
- Crash the phone.
Without IPsec, you should be able to eavesdrop on phone calls with a packet sniffer. In theory, you could redirect phone calls or change voice mail settings, but these are truly malicious activities and I did not research how to do this. These actions would require IP spoofing which is beyond the scope of this article.
How-To
Start with physical access to the phones and assume each phone is password protected.
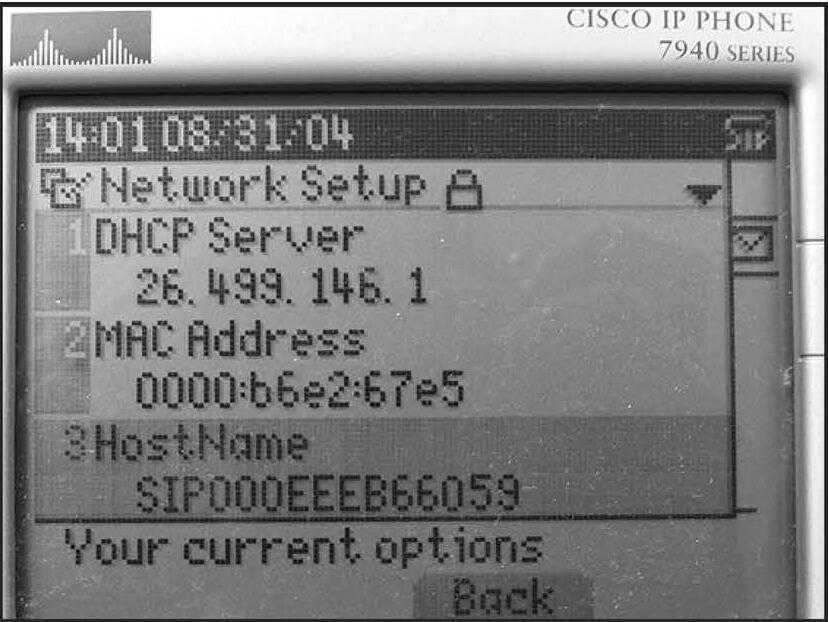
Get the IP address, hostname, and TFTP server for each phone by pressing the configuration button (the one with the picture of the check box) and selecting "Network Configuration".
The hostname will be something like SIP000CAED39328. If you do not have physical access to the phone, then you will need to sniff for this information.
The network configuration screen showing the DHCP server, MAC address, and hostname. Notice the "Lock" icon in next to the title, indicating that we cannot change the settings yet.
Next, use a TFTP client to retrieve the files RingList.DAT, SIPDefault.CNF, and SIPXXXXXXXXXXX.CNF where the X represent the hostname of the phone.
Replace SIP with SCCP or MGCP if your server uses one of these protocols (Ref. #1).
The configuration files are plain text files containing the server settings, phone numbers, Telnet level, and an unencrypted password. Settings are the default configuration file and may be overridden in each phone's configuration file.
This password also allows you to change configuration settings via the phone's menus by selecting the "Unlock Configuration" option in the configuration menu. You may also Telnet to the phone using the IP address and password. From here, you can execute many commands.
A full list of commands is available at (Ref. #2).
The test key command is the most fun. Pressing the volume buttons causes the phone to ring. You can change settings such as ringtones by simulating the navigation keys. It is possible to pick up the speakerphone and dial, then connect to the destination phone and instruct it to pick up.
Changing Ring Tones and Other Settings
You can select any of the standard ring tones using the phone or via Telnet.
RingList.DAT contains the description and file name for each ring tone. You can download the ring tone files via TFTP, but you cannot upload new ones to the server. The ring tone files are 8 kHz 8-bit µ-law audio files (<= 2 seconds long) (Ref. #3).
Using the existing ring tones is neat, but making your own is very cool.
Since you cannot upload files to the TFTP server, to use your own ring tones you need to set up your own TFTP server and direct the phone to use it.
In the phone's configuration screen is a setting "Alternate TFTP." Set this to "Yes". Then change the "TFTP Server" setting to contain the IP address of your server.
Now you can serve up your own firmware, ring tones, and configuration files. Serving your own configuration file allows you to change the URL for the logo on the display, the URL for the corporate directory, and the phone number for the voice mail.
Logo files must be 8-bit BMP files even though the LCD is black-and-white (Ref. #4).
It looks like the corporate directory browser works like a minimal text-only web browser. In this particular office, the phones did not have working DHCP so the HTTP server for the logo had to be a single-homed HTTP server that was accessible by IP.
Conclusions
IP phones are gaining in popularity since they are becoming versatile, powerful, and easy to install.
Price-wise, they are competing very effectively against existing PBX systems. Expect to see rapid growth in the future. However, expect to see more stringent security in place now that the phones ship with IPsec.
For now, have fun by listening in on meetings and making your coworkers' phones taunt them.
References
1.) Information on the boot-up process and the files residing on the server: Converting a Cisco 7940/7960 SCCP Phone to a SIP Phone and the Reverse Process
2.) Telnet commands, monitoring options, and troubleshooting tips: Monitoring Cisco SIP IP Phones (Versions 6.0 to 7.4)
3.) Physical phone setup, ring tones: Getting Started with Your Cisco SIP IP Phone (Version 1.0)
4.) Logos, messages, directories, ring tones, general information, and links: Configuring Cisco 79xx Phones with Asterisk
Cisco SIP IP Phone Administrator Guide Release 6.0, 6.1, 7.0, 7.1, 7.2, 7.3, 7.4 (March, 2005)
CLI Commands - Example
reset Reboot the phone and reload the firmware via TFTP.
exit Close the telnet session.
test open Enter hacking mode.
test close Exit hacking mode.
test [key] Simulate pressing key X on the phone. Keys can be:
voldn: Volume down
volup: Volume up
headset: Headset
spkr: Toggle speakerphone
mute: Mute
info: Info
msgs: Messages
serv: Services
dir: Directories
set: Settings
navup: Navigate up
navdn: Navigate down
test string String can be any number of 0..9, #, and *.
This allows you to control the menus to dial.
test onhook Place the phone on or off-hook, as though someone
test offhook picked it up. Can be used to answer calls.
Improper use of this can cause the phone to confuse on and
off-hook (picking up the receiver can become the
on-hook state, and vice-versa)
test ? Ask the phone what keys it supports. This is useful
test help if your phone has additional navigation "soft" keys.
|