Using aircrack-ng against WPA encryption (Tutorial)
By Click Death Squad (C.D.S.)
Revision 1.0
The goal of this tutorial is to demonstrate how easily your own WPA key can be disclosed. This method of breaking WPA keys is a little different than attacking a WEP secured network. While breaking WEP keys requires you to run an attack and brute force a key while connected to an access point, WPA does not. In fact, it is much simpler to break a WPA key, because it only takes 1 captured packet. Please note that this method only works with WPA-PSK networks using TKIP. The idea is that when a client connects to a WPA secured network, the wireless access point and client computer will "handshake" and mutually exchange a PSK (Pre Shared Key) in a 4-way exchange. If you happen to be capturing data, you can save a packet of the encrypted handshake taking place. Once you have captured this handshake, you can run an offline dictionary attack and break the key. This is particularly disturbing, because it would only take an attacker but a few moments to drive by a wireless access point and capture a single handshake, then go crack the key at their own leisure.
The question arises: How do you capture a 4-way TKIP handshake without sitting and watching traffic for hours and hours, waiting for a client to connect to a network? The solution is simple. By watching a wireless network to see which computers are already authenticated using services, you can forcefully deauthenticate those clients and force them to reconnect back up. In the process of re-exchanging the encrypted WPA key, you will capture a handshake. The WPA attack does not work on wireless networks which have no clients connected to it. In order to forcefully capture a 4-way handshake, you will need to deauthenticate a client computer that is actively using services, forcing it to exchange the WPA key and in turn capturing the handshake that can be decrypted. Try testing this on your own network with 1 or more computers connected and see just how easily this can be accomplished.
In this example, we used an Intel IGN5100 card, and all the commands issued are given in quotes, with the result of the commands being listed in grey.
After each step, a screenshot is given so you may compare your output
to what should be happening. Please note that not all the screenshots
contain the exact same data which is given in the example, they are
merely for reference purposes.
Tools you will need to accomplish this task:
- System with aircrack-ng installed, or a Backtrack 3 CD
- Wireless network encrypted with a WPA passphrase (your own) that you can test
- Network card that supports packet injection, such as an Intel IGN-5100 based device
- Basic Linux networking skills and command line capabilities
- A cold beer
Step 1: Put the interface in monitor mode.
Assuming you are booted up and ready to go, you'll need to put the interface in monitor mode and get ready to start dumping packets from your target network. We are also assuming that you know the ESSID of your network, the BSSID and channel also. If you don't know these values, refer to the "Aircrack-ng against WEP" tutorial which shows you how to scan and determine this information. Put the network card in monitor mode and get ready to watch some handshaking.
"airmon-ng start wlan0" ### where wlan0 is your network interface device.
Step 2: Start capturing traffic for the target access point and prepare to deauthenticate a client.
You need to start dumping all the packets in order to capture a 4-way handshake for the target network. You can do this by telling airodump-ng exactly which channel to listen on, and to filter out all other wireless devices besides the one you are testing. It would also be wise to pass the "--showack" flag so that way you can ensure your client computer is acknowleding your request to deauthenticate it from the wireless access point. Start dumping all packets going to and from the target wireless access point, and be sure to leave this window open and running.
"airodump-ng -c 10 --bssid 00:1D:7E:56:FD:F6 --showack -w handshake mon0" ### where "-c" specifies the channel to listen on, "--bssid" specifies the target MAC address, "--showack" tells airodump to give verbose ACK related information and "-w" specifies the file to save packets (handshake) to.
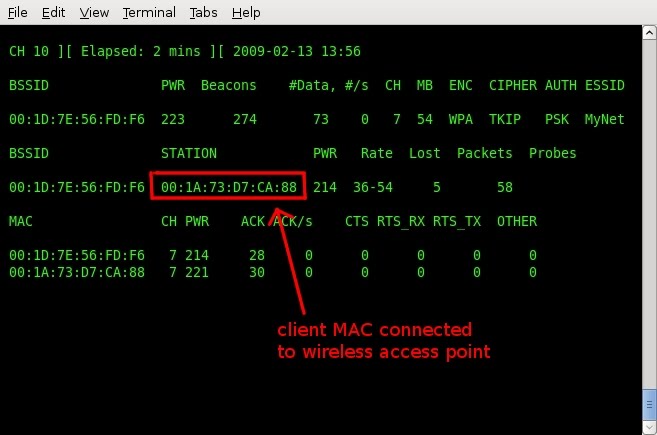
In the example screenshot, you can see all the related information for the target access point. You can also see some other important information that you will need to know in order to complete the attack, which is the MAC address of a client who is already connected to the WPA secured network. Again, be sure to leave this window open and continually dump traffic so that you can complete the next step, which is to deauthenticate this client who is connected and actively using the internet.
Step 3: Deauthenticate the client who is already connected and force them to re-exchange the WPA key.
You can see in the screenshot that we have a victim who is already connected up. They will provide the 4-way handshake for us, once they are disconnected from the wireless access point. Assuming you still have a terminal window open dumping traffic, open a new terminal and deauthenticate the victim from the target network.
"aireplay-ng -0 5 -a 00:1D:7E:56:FD:F6 -c 00:1A:73:D7:CA:88 mon0" ### where "-0 5" tells aireplay to inject deauthentication packets (5 of them), "-a" is the wireless access point MAC address and "-c" is the client (victim) MAC address.
A successful deauthentication attack will show ACKs, which indicates that the victim who is connected to the access point has acknowledged the disconnect we just issued. It is possible to send just 1 deauthentication request, but depending on the range of you to the target wireless network sometimes more than 1 request is needed. We chose to inject a handful of deauthentication requests to ensure that the vicim gets the message.
Step 4: Ensure you have captured the 4-way handshake.
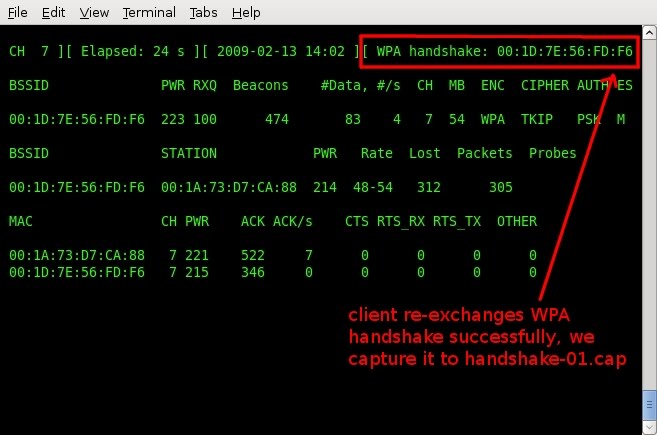
Now that you deauthenticated a client from the wireless network, that client will re-exchange the WPA key. Because you have your terminal window still open and dumping traffic, you should have captured this handshake.
Airodump will show the captured handshake in the top right hand corner. Now that you captured the packet you need, you can close this window and proceed to break the WPA key.
Step 5: Prepare your dictionary for the attack.
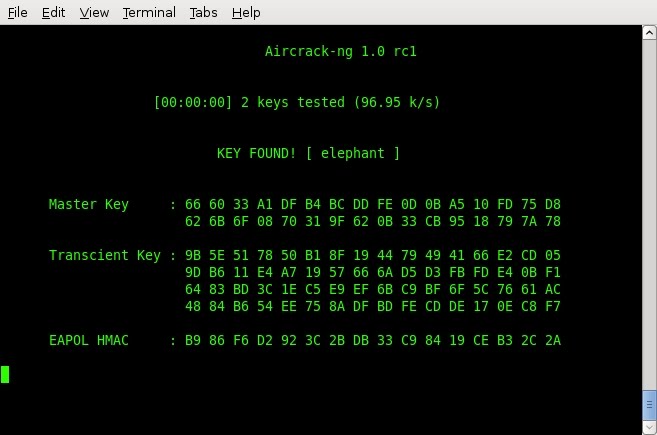
The whole assumption with this tutorial is that you are testing your own network. Let's assume that because this is your network, you also know what the WPA passphrase is, because you set it up. In the example screenshot, we compiled a file called "dictionary.txt" which contains a few entries of possible passphrases that might have been used. The passphrase for our test network was "elephant" so we included it in our dictionary file. Also take note that when encrypting a network with WPA, a passphrase must be a minimum of 8 characters, with a maximum of 64. The whole reason you should not use dictionary based words or phrases is because they can be easily broken. Knowing what your password is for your own network, compile a dictionary file and include the real password somewhere in the middle.
Step 6: Run aircrack-ng and break your key with the dictionary you compiled and the 4-way handshake you captured.
This is the easiest step. Tell aircrack to use your dictionary file and encrypt each entry, then compare it with the encrypted data which was captured during the handshake. On a fast computer (dual core, 4GB RAM) you can achieve up to 300 tries per second. Depending on how large the dictionary file is, having a fast computer will come in handy. All you need to do here is tell aircrack which cracking mode to use and where the dictionary file is located.
"aircrack-ng -a 2 -w dictionary.txt handshake-01.cap" ### where "-a 2" specifies WPA cracking mode and "-w" specifies the dictionary file to use.
There you have it. WPA-TKIP key has been successfully decrypted. Again, all it takes is capturing a single handshake and then running a dictionary attack in your spare time. If an attacker drove by your house and captured a handshake, it could mean game over. What steps can you take to protect yourself from this type of attack? The most obvious choice is to secure your network with a very difficult to guess passphrase. Dictionary words or combinations of numbers that might be easily guessable are all bad ideas when choosing a WPA passphrase. Try to pick something easy to remember, yet difficult to guess, preferrably at least 12 characters long. The second aspect to take into consideration is that WPA and WPA2 both use the same encryption scheme. If you really want to prevent this type of attack from being carried out, DO NOT use the TKIP key exchange method. Most wireless routers give you the option of using TKIP or AES for the key exchange. Because WPA and WPA2 both are vulnerable to the same attack when exchanging keys using TKIP, utilizing AES would be the preferred method. There are currently no public known weaknesses using AES, which makes it much safer. If you pick strong passwords and don't use TKIP, you should be fine. Think before you type, and keep your network safe!